This article is more than 1 year old
Weather forecast: WiFi storms make meteorologists look mad
Boffins are finding ways to stop WiFi messing with weather stations
A problem in a world of global WiFi equipment is that global spectrum allocations aren't consistent, and in some places, kit clashes with applications like weather radar. A group of Austrian researchers is looking at how to clean up radar images spoiled by nearby WiFi kit.
In a paper published on the Arxiv pre-print server, the scientists note that it's not just 5 GHz WiFi that causes artefacts on images: air traffic control radars and topology also cause problems for weather radar.
Led by Harald Ganster of Joanneum Research in Austria, the research found that a third of images from one weather station in the mountainous country suffered wireless LAN interference, with disturbance like that shown below present in “2713 from 8928 images”.
“Improvement of WXR [weather radar – El Reg] images - by combining them with other sensors in order to complete concealed zones and eliminate interfering signals without losing important meteorological information - is essential for an accurate prediction of weather phenomenons and atmospheric conditions”, they write.
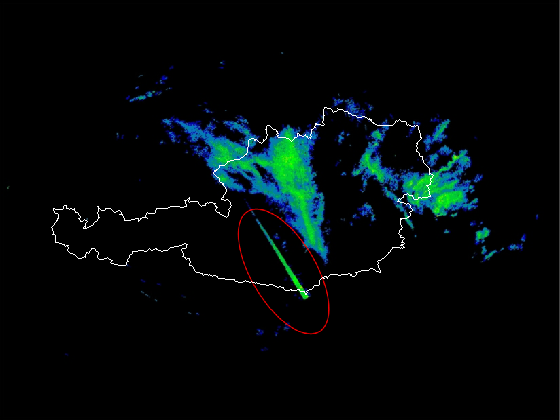
WiFi interference on Austrian weather radar
The algorithm developed by Ganster's group is designed to identify such artefacts in the radar images so they can be removed. Geometry is helpful here: something like WiFi, whose interference appears as a straight line, can be classified, turned into a vertical line, and removed, as can the speckle coming from air traffic radars.
The other aspect of the work is to fill in shadows in the radar. They do this by taking long-term data from meteorological satellite images, and stitching that data – which they refer to as “meteorologically reasonable” – back into the real-time radar data.
The aim of that part of the work is to provide a model that can reasonably serve as a proxy for the real-time data.
It still doesn't provide an explanation, however, for artefacts like Australia's “Rottnest Monster”, which set the country afire with speculation in February.
That ended up being attributed to a defence training exercise. ®
