This article is more than 1 year old
Freescale: Cloudy dumb sensors? Nope, not OUR smart Internet of Things
Vehicle-to-X is next big digital gold rush – plus security and privacy, of course
Rip up your data centre blueprints
Admittedly, Freescale would want to highlight its capacity to support different networking protocols, and goes further by taking a swipe at the x86 architecture. Wainwright predicts a re-engineering of data centres with different breeds of processors emerging to accommodate the flow of information from the Internet of Things.
“One of the things that’s interesting about the Internet of Things is: does anybody really care any more about which processor architecture is out there? Does anybody care if it’s MIPS, ARM or x86? Certainly in the world of ARM, the opportunity with this explosive data requirement is really being seen as a way to break the x86 monopoly that’s existed there forever really in IT applications.”
That’s not all wishful thinking either, as the low power consumption of ARM processors is gaining traction with the likes of AMD and Dell, among others, developing their own ARM server ecosystems.
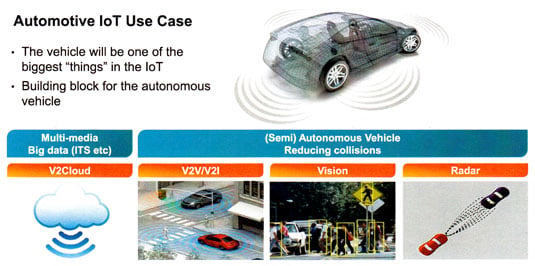
Freescale Connected Intelligence automotive
Back in the Freescale heartland of automative chips, Wainwright talked of V2Cloud (vehicle to cloud), V2V (vehicle to vehicle), V2I (vehicle to infrastructure) as examples of IoT in transport. Multimedia V2Cloud services are already in place, with audio and video streamed into cars. Services such as traffic management, under the umbrella of the Intelligent Transportation System (ITS), also form part of the vehicle-to-cloud experience, with some tasks relying on Big Data to manage navigation, traffic news and control.
Yet it’s the opportunity for vehicle-to-vehicle and vehicle-to-infrastructure transportation that has really got this business excited. These two approaches are set to unfold into semi-autonomous and, eventually, fully autonomous driving. Wainwright outlined latency and redundancy as among the technological challenges – but the biggest problem he could foresee had more to do with hot air than bits and chips.
Viennese whirl
Legislation and in particular the Vienna Convention on Road Traffic (1968) he singled out as “the classic gotcha for autonomous driving”. One of the issues here being that the driver must always be in control of the vehicle – this appears in Article 8 of the convention along with other similar criteria [PDF here]. However, Wainwright is optimistic that the court of public opinion will eventually enable suitable amendments as the advantages reveal themselves.

The rules of the road, 1968-style
"That fact that there is a big liability issue tends to go away when you’re used to using utilities that give you a real benefit as a person driving a car," he said.
"Self-park is the obvious one that’s already started – a pretty easy application. Platooning will be the next one, when you’re talking about high density traffic. As people get to the mode of wanting to avail themselves of these opportunities, I think the challenge will come from the sheer weight of adoption."
Beyond V2V and V2I there is vision and radar, with vision identifying signs, people, objects and other features – much like face recognition on tags on photos – and relaying it to a user interface or audible warning. Radar’s reach could benefit high speed driving or for navigating other hazards such as fog and, used together, vision and radar have great potential. It’s a set up that sees a dramatic increase in vehicle sensor technology controlled by central processing within the car and along with some connection to infrastructure.
The snag for this new age of transportation is dealing with the latency issues. There’s no point in having a radar in fog that tells you there’s a truck coming the other way that takes eight seconds to notify you when it’s six seconds to impact. Connected Intelligence might not seem so clever if it’s dogged by latency.
