This article is more than 1 year old
London Tube has new stop at Azure Station
Microsoft blurs lines between Internet of Things and embedded Windows
Microsoft has claimed that while the rest of the industry is falling for or projecting Internet of Things (IoT) hype, it is quietly delivering on the concept's promise right under many Reg readers' feet in the form of a new Azure-powered monitoring rig for the London Underground.
Speaking at a press event in Sydney today, general manager of marketing for Microsoft's commercial Internet of Things Barb Edson said Redmond has been using the term IoT for ages, but hasn't dared to utter it in public. Challenged by The Reg as to whether a user of embedded Windows in remotely-monitored industrial robots would have been described as an IoT practitioner a year ago, Edson – after a couple of dissembling PR-isms - eventually said that, yes, within Microsoft's walls such an application would most certainly have attracted the acronym long before the current wave of hype broke.
Microsoft then went on to display what it called an IoT showcase but which relied on small form factor industrial PCs in a variety of applications, rather than the lesser sensors often imagined as the IOT's nodes. One, a fridge intended for deployment by Coca-Cola Amatil, Australia's licensed Coke bottler, featured a transparent LED into which ads for sugary drinks were pumped in a mode that will be familiar to practitioners of digital signage. The fridge also packed a camera that allowed it to detect the faces of passers-by, so it could then put them on-screen complete with a digital wig on their heads in order to get them to pay more attention to the drinks within. Spookily, the camera was used to analyse images of punters as they passed so that Coca-Cola Amatil could guess at the age and gender of those who found an interactive Coke fridge compelling.
Microsoft's claim for IoT-ness for such applications rests on their use of the Azure Intelligent Systems Service (AISS), a cloudy caper announced at the recent Build conference and which offers the chance to gather data from numerous sources and integrate them so they can be subjected to analysis by other Microsoft services like Azure Hindsight and Power BI for Office 365.
Microsoft's poster child for AISS is telent, the UK-based technology services company that has a long history of SCADA work and an engagement with several UK transport companies. telent has worked with another outfit called CGI to pump its existing network of sensors into the AISS, producing a tool that offers the chance to view a map of the Tube complete with flags for equipment that needs attention.
Here's a grainy, slightly-sideways look at how that works.
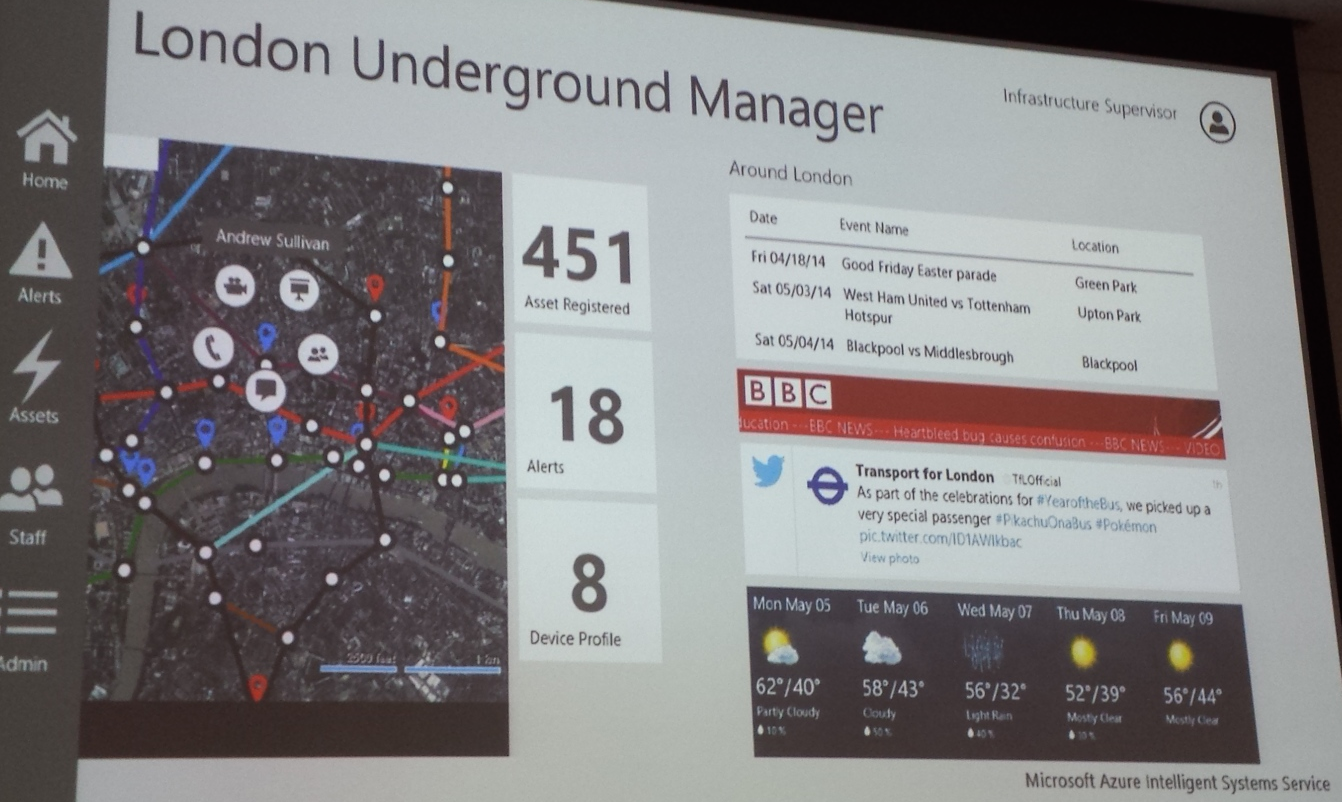
The London Underground, as visible to managers trying to spot faults with the assistance of Microsoft's Azure Intelligent Systems Service
Once managers spot a fault, they can then enjoy a closer look at the station where it is located.
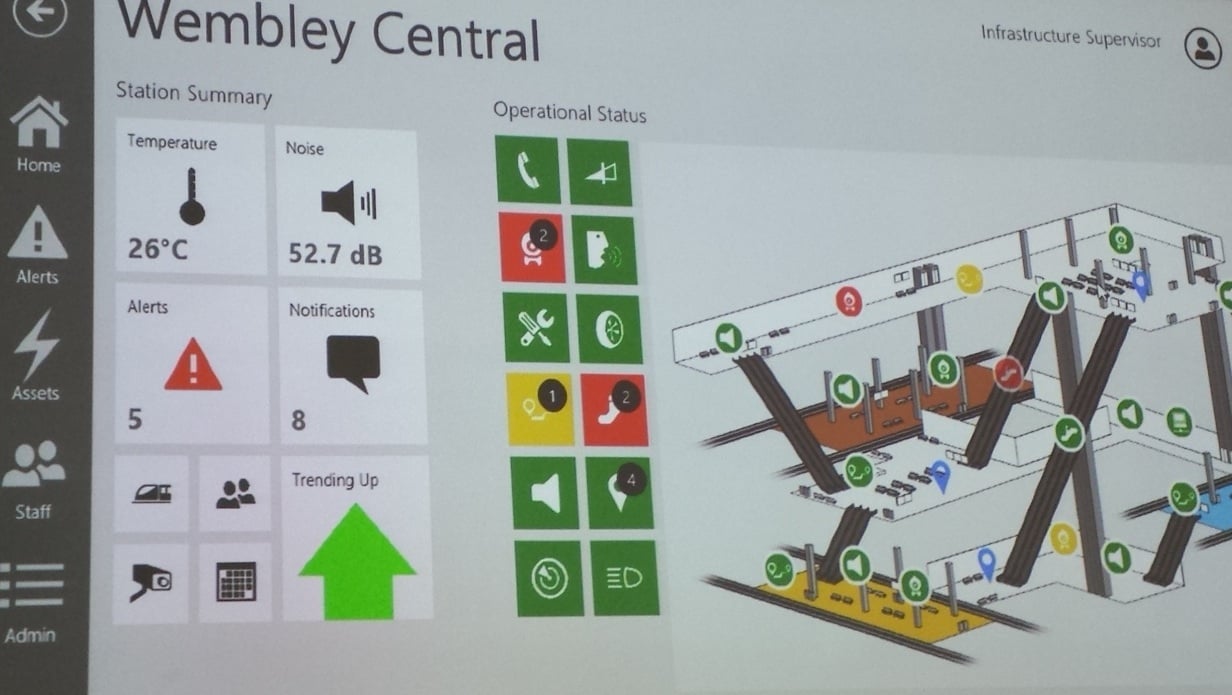
Wembley Central station, viewed as a home for Internet-connected things
Clicking on the faulty item then offers the screen below, to help determine just what the problem is and its likely impact.
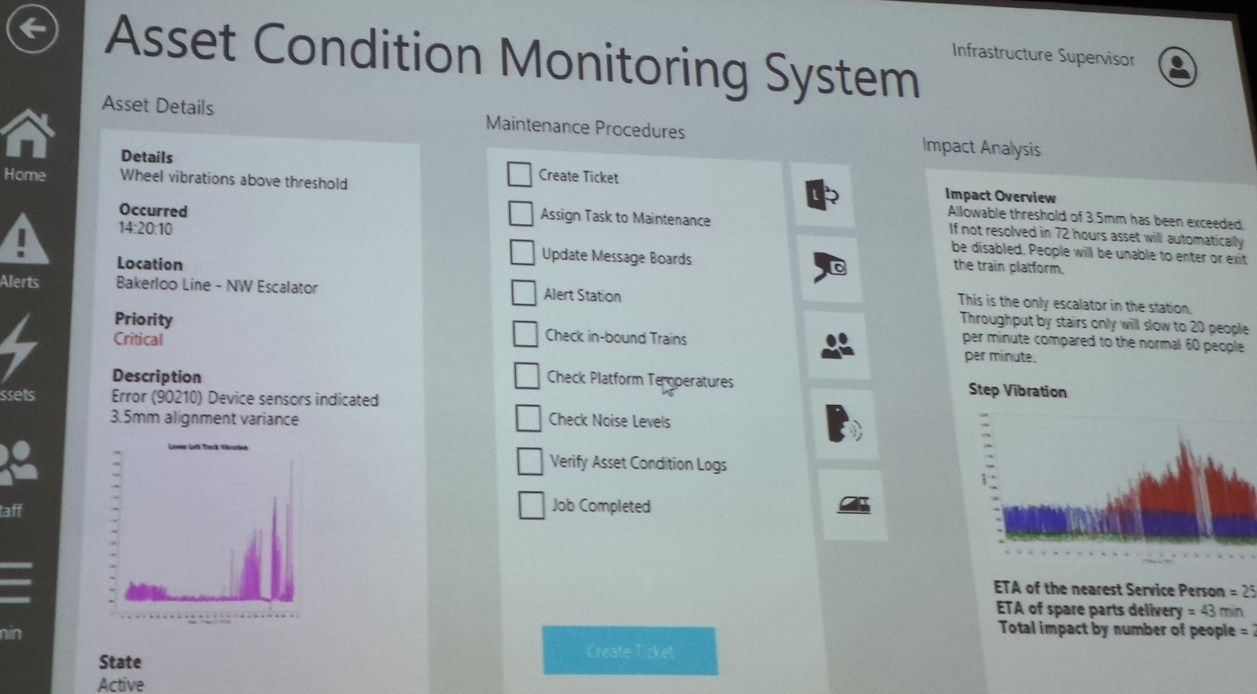
A report on a faulty escalator somewhere on the London Underground
The demo was apparently cobbled together by a small team in two weeks and is operational and covers thousands of sensors, but is not a frontline tool and is not connecting to devices across all of the Underground.
The demo was impressive, but also not much more than a nice dashboard for existing sensor systems. Don't take that as a criticism of Microsoft. But do, perhaps, wonder if other folks clambering aboard the IoT bandwagon have anything more novel to offer. ®
