This article is more than 1 year old
No, it's not a boy band, it's a biz backup suite: A dig into Druva inSync
Keeping data safe
Review Druva seems to be on a quest right now to get its name seen by as many people as possible; lately I have been bombarded by more inSync banner ads than I can shake a stick at. So it came as no surprise when the Reg asked me to have a look at what the backup and management biz does – and whether it is any good at it.
The inSync suite has four components, covering endpoint backup, data loss prevention, file sharing and data governance.
The latter is a set of protection mechanisms that wrap around the others to provide sharing controls, prevent administrators from viewing sensitive data and so on.
You have the option to license the software for an on-premise installation or to use Druva's cloud installation (which, as it happens, is hosted in Amazon's AWS cloud service – have I just invented the term “cloud squared”, or maybe “cloud in a cloud” or “CinC”?) Given my penchant for all things cloud, I went for the latter.
Setting it up
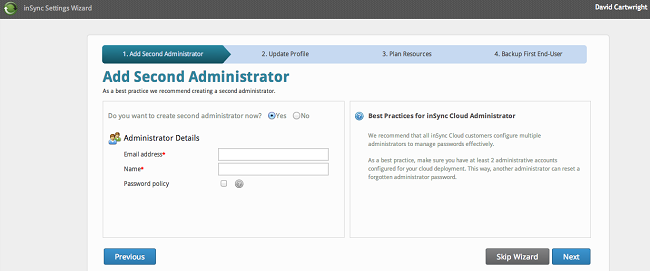
Once setup is done and you have received your admin credentials, you walk through the setup wizard. First, you are prompted to create a second admin account, which the service is pretty insistent is an important step.
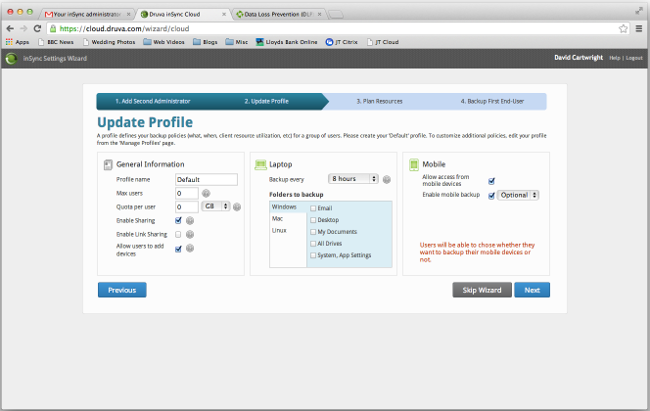
Next comes the facility to configure the default profile, which has three sections. First is the basic setup, including disk quota for users and some tickboxes that dictate things such as whether users can use file sharing or add devices to the service themselves.
Then there's a section covering default backup schedules and file types for laptop machines; and finally there are a couple of options covering mobile devices.
Click "Next" and you are into resource configuration, where you can set bandwidth and CPU caps for client machines, control some user-access capabilities and set the retention policy for saved data.
Finally you are invited to back up your first end-user; give it the user's name and email and it throws that person instructions on what to do.
To back up a device you will need to download the appropriate client. These are available for Mac OS X, Windows, Ubuntu and CentOS Linux, plus Windows Mobile, Android and iOS mobile devices.
Mac, back and stack
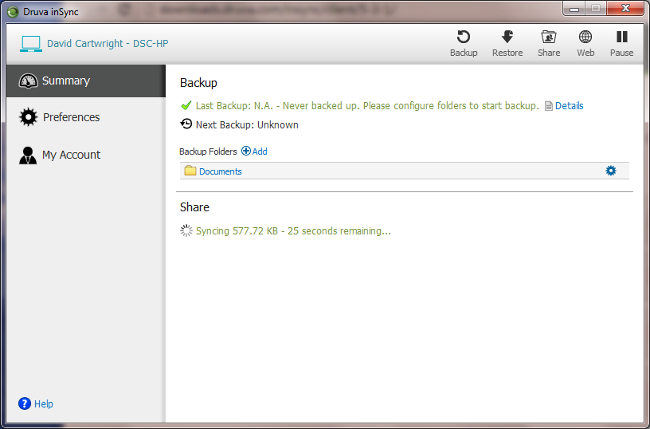
The Windows client... a 45MB download later
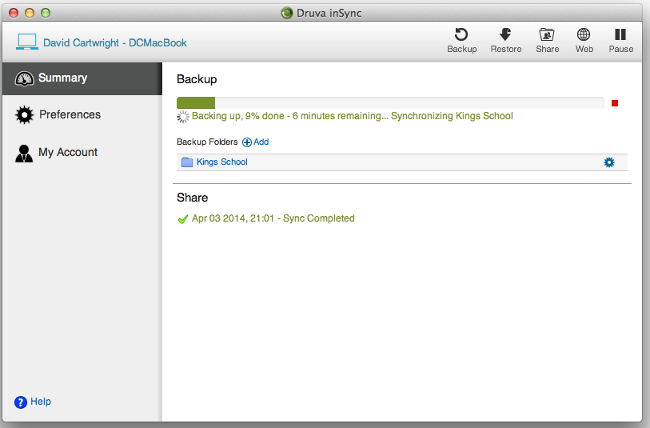
I tried the Mac OS, Windows and iPhone flavours. The first two are 45MB downloads, so it took a little while to download them.
The backup client, no matter what the platform, is simplicity itself. The GUI is clear and intuitive (except, perhaps, for the option to remove a folder from the backup set if, like me, you clicked the wrong thing) and it is easy enough to get your folder sets configured and synchronised with the backup server.
Perhaps the only addition I'd like is to see the total folder size beside each item in the GUI, just so you can have a bit of a sanity check about what you have told it to back up.