This article is more than 1 year old
Walking while texting can – OUCH! – end badly, say boffins
Prodding your mobe slows you down and limits your vision
Scientists have proved what anyone walking down a crowded street in modern city knows: those who gaze at their phones while ambulating are a danger to themselves and others.
Detailed here at PLOS ONE in research titled “Texting and Walking: Strategies for Postural Control and Implications for Safety”, the authors explain that they subjected 26 test subjects to experiments in which they measured normal walking, walking while reading a phone and walking while sending a text message. Subjects were screened to ensure they were familiar with modern phones with QWERTY keyboards.
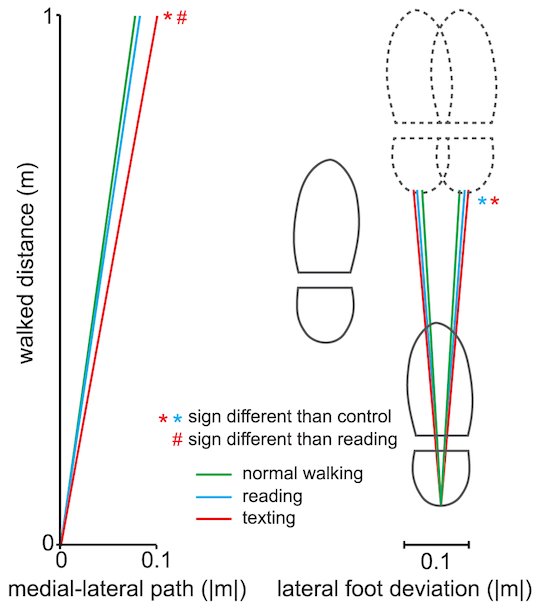
Eight cameras were used to record subjects' movement on an ~8.5m course and they captured all sorts of data: the paper says “Relative motion between the thorax and head (neck motion), and between pelvis and thorax (trunk motion) were obtained by subtracting the time series of the relevant angles of the lower segment from the higher segment.”
Those measurements lead to a very detailed discussion of kinematics and other exercise-related stuff that make the innards of a CPU seem comfortingly simple. Long story short, walking while looking at or using a phone changes your gait and reduces your ability to walk in straight line, partly because your head actually moves a bit more than is usually the case.
“In a pedestrian environment inability to maintain a straight path would be likely to increase potential for collisions, trips and traffic accidents,” the paper suggests, backing up the observation that “Nine of 26 (35%) participants reported a previous accident while texting on their mobile phone, including falls, trips and collisions with obstacles or other individuals”.
So there you have it: that person you had to avoid on the way home yesterday lest their insistence on doing something with their phone led to a shirt-fronting is a dangerous symptom of the modern world. Something clearly Must Be Done. Unless they were reading The Reg, in which case all is forgiven. ®
TXTing while walking sends you on a dangerous course
