This article is more than 1 year old
EMC tries to snuff out SolidFire before tomorrow's XtremIO-gasm
Rivals try to knock each other out with storage posers
EMC has readied some XtremIO competitive knock-offs to help the Hopkinton storage giant's reps and channel partners dislodge rival SolidFire from their prospects’ minds.
The main knock-off points are:
- XtremIO utilises an innovative flash specific data protection algorithm providing double failure protection with only 8 per cent capacity overhead. SolidFire replicates data within a cluster wasting at least ½ or up to 3/4th raw capacity.
- XtremIO utilises eMLC SSDs delivering enterprise reliability and endurance and does not move data once written. SolidFire uses cMLC consumer grade flash and experiences write amplification due to garbage collection.
- XtremIO’s content aware architecture delivers up to 250K IOPS per node with <1 ms latency performance during real world workloads. SolidFire claims best case 50K IOPS per node with <2 ms latency performance.
- XtremIO has a no single point of failure (NSPOF) design with all drives accessible to active/active storage processors. SolidFire nodes have a single controller so a failure disables the entire node and up to 20 per cent of capacity.
- XtremIO provides iSCSI and Fibre Channel ports that concurrently support access to storage LUNs. SolidFire only supports iSCSI for storage access.
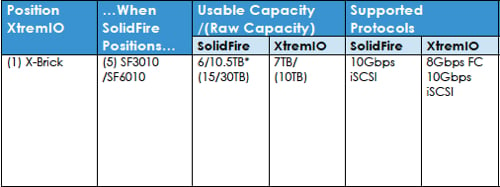
XtremIO product positioning vs SolidFire
Here are some of the embarrassing questions with which reps are prepped to grill XtremIO prospects on SolidFire:
- Ask SolidFire about their <50 per cent raw capacity per node after 1 to 4 replicas (default is 2) for data protection and its performance impact on IO completion for writes. XtremIO raw capacity is more than 70 per cent due to an efficient data protection algorithm with no mirroring and no performance reductions.
- Ask SolidFire about their flexibility to start with a configuration smaller than 5 nodes. XtremIO starts with a single HA X-Brick for an attractive entry point.
- Ask SolidFire about the failure rates of consumer grade MLC flash memory and why they are not using eMLC for enterprise SSD resilience. XtremIO’s use of enterprise grade eMLC flash provides a major advantage in flash reliability and superior endurance from XtremIO write abatement techniques.
SolidFire CEO Dave Wright had this to say about the EMC document: "[It] is just ridiculous (and inaccurate) enough that we feel like we need to respond publicly, so we're going to be putting up a blog post ... It's not fully point-by-point, because there is frankly so much crap in there we ran out of space. It's clear that EMC is really grasping at straws to try and make XtremIO look competitive."
The blog identifies the EMC community website where the anti-SolidFire doc was to be found but access has been closed off.
Wright rebuts many of the EMC points, saying indicating most of them are wrong, and concludes: "SolidFire has certainly made different design decisions in some areas (like shared-nothing vs dual-controllers), [so] there are strong advantages to the SolidFire approach in the use cases and environments we focus on. The SolidFire system leads the industry in flash density and cost-effectiveness, with a range of functionality such as Guaranteed QoS that can’t be found in any storage system." ®
Bootnote
Here are the other embarrassing questions EMC's other doc listed:
- Ask SolidFire about the impact of using the same 10Gb iSCSI network for cluster traffic plus read/write storage traffic (especially during recovery time). XtremIO utilises a dedicated redundant 40Gbs InfiniBand RDMA fabric for managing the cluster and separate iSCSI and FC networks for host IO.
- Ask SolidFire why their latency is only <2 ms? XtremIO can deliver <1 ms latency for all workloads even as array capacity utilisation levels increase.
- Ask SolidFire to show scalability to large node counts as all their customer wins to date are relatively small.
- Ask SolidFire to compare their 1.5kW energy efficiency for 5 nodes to XtremIO. A single X-Brick is half the power footprint at 750 watts.
And here are pointed questions SolidFire suggests XtremIO prospects ask EMC:
- Can you expand (or shrink) an existing cluster?
- Why does each X-brick require a UPS?
- What’s the performance impact of a controller failure?
- How much will it cost?
