This article is more than 1 year old
PUNISHMENT gluttons: The Dr Who monsters that come back for more
Data Visualisation: The Doctor’s most commonly returning foes
Doctor Who @ 50 Given the Doctor’s propensity for making enemies, he has faced relatively few more than twice. This is perhaps not surprising for someone who can travel anywhere in the whole history of the entire universe – the chances of bumping into someone again should be low.
But the demands of making an adventure TV series mean return matches with popular adversaries are inevitable. It surely follows that more than one showing up in a story would be even more popular, and if they were actually working together against the Doctor, well, he'd have no chance, would he?
This chart shows the story links between major returning foes. Adversaries are included if they’ve appeared in three or more stories. The outer ring is proportional to each race’s number of appearances, clockwise in the order in which they first appeared. Stories are counted if they include newly recorded material, not just past clips or photographs.
Incidentally, ‘Time Lords’ counts any story in which a Gallifreyan other than the Doctor, Romana or the Master appeared. Not all races were villainous in every story but they are counted anyway.
The coloured links indicate appearances by more than one of these monsters in the same story. These may be in unconnected scenes or as a unified force.
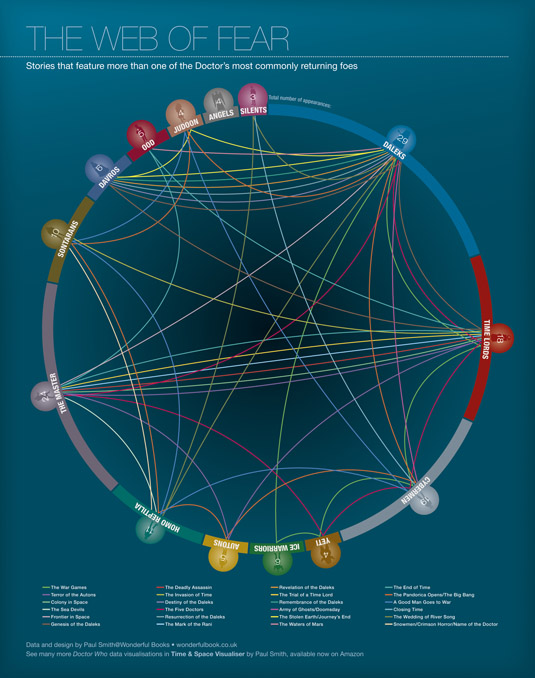
Click to see the visualisation full size
Source: Wonderful Books
The story with the most recurring enemies is, not surprisingly, The Pandorica Opens, in which the Daleks, Cybermen, Autons, Silurians, Sontarans and Judoon join many other one-off races in an alliance against the Doctor to prevent him, they believe, from destroying the universe.
The Five Doctors features five recurring adversaries, each transported to the Gallifreyan Death Zone to battle the Doctor on his birthday, as does The War Games, thanks to the Doctor’s defence plea that all the nasty creatures in the universe need to be put in their place.
There are four major monster appearances in A Good Man Goes to War, although the Cybermen were not involved with the others, who were actually fighting on the Doctor’s side for once.
The Weeping Angels are the only enemy to have appeared more than twice but never in a story with any other. ®
The image comes from Time & Space Visualiser: The Story and History of Doctor Who as Data Visualisations by Paul Smith, published by Wonderful Books and available through Amazon UK and Amazon US.
