This article is more than 1 year old
Failover a dependency rich infrastructure and you bork the lot, right? Not any more
Neverfail rolls out network-mapping Architect tool
Business continuity bods Neverfail have looked through a keyhole and found themselves a whole new universe. Its Heartbeat business continuity product needs a bit of infrastructure understanding to set up, but there's no tool available to give you that understanding. Until now, thanks to Neverfail's IT Continuity Architect.
IT wants server-based apps to carry on running with access to their data if a server fails; that's business continuity from its point of view. Only it isn't business continuity; it's server continuity. The business wants that part of its operation that's dependent on the apps in a server to keep on operating if the server fails.
It's a simple enough concept but the trouble is there is a whole universe of dependencies in a software app like SharePoint or Exchange – dependencies on component software items and data stores – which might be located on different physical or virtual servers. And the data those dependencies handle may be kept in direct-attached or shared storage. Blindly failover a failed component server in such an app infrastructure and you could break the app and screw up the business' core operations.
The need is to understand the component dependencies in a business operation's IT infrastructure and map out the business continuity needs, so that when a server fails the process recovers from that failure with dependencies intact.
The stages involved in this are:-
- Component discovery
- Dependency mapping
- Business service mapping (business rules)
- Protection analysis
- Monitoring and reporting.
Neverfail's IT Continuity Architect (“Architect” for short) firstly has to discover the components and their dependencies. It does so by looking at server ports, without needing any agent software installed.
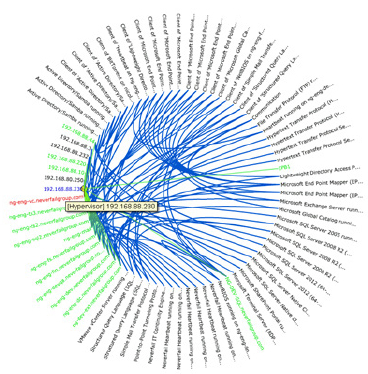
Neverfail IT Continuity Architect Dependency Graph
The discovery phase takes around 30 - 50 minutes. Architect then uses these dependencies to build a picture of what the infrastructure contains and builds a dependency graph. The software then maps the business' operations to this infrastructure and then – the ultimate aim – it can rate the delivered protection in terms of its effect on the business' operations.
What is its ability to meet service level agreements (SLAs) and how can that be monitored?
Architect can produce a dependency protection heatmap; a graphical depiction of dependencies and their protection level using the colours red, yellow, and green, in a traffic light style system.
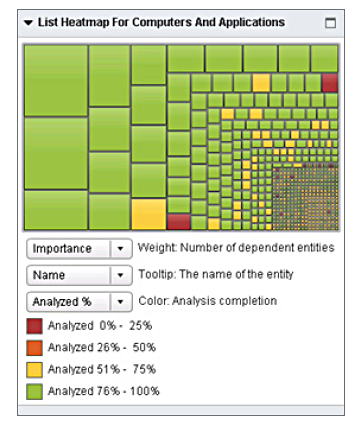
Neverfail IT Continuity Architect heatmap. The bigger the oblong the more important the dependency.
Neverfail reckons its business service mapping is unique. The Continuity Architect product will automatically detect protection arrangements in place, and once the RPO (Recovery Point Objective) and RTO (Recovery Time Objective) items are known, can tell the admin staff if they can be met.
Architect will be available on a subscription basis with perpetual licensing possible as an alternative. A side benefit is that Architect will provide the information needed for a clean and easier installation of the Heartbeat product.
Heartbeat is OEM'd by VMware as its vCentre Server Heartbeat offering. Will IT Continuity Architect be picked up and OEM'd too? Time will tell.
It looks to a unique and informative view of business operations and their IT infrastructure dependencies which should improve business continuity management. As infrastructures get more complicated component-wise then the need for Architect-like functionality should grow.
Neverfail could be sticking its Architect key into a keyhole and so opening a door to satisfy a wide need. Sounds good. Grab a free trial here. ®
