This article is more than 1 year old
Ten top new games for phones ’n’ slabs
August Bank holiday weekend time-wasters
Into The Dead

A variation on the endless runner game, the idea here is to dodge zombies while running at them from a first-person perspective. The challenge comes with the ever-increasing density of the undead and their unwelcome habit of looming up out of the long grass or from behind trees. Run into one head on and you die. No second chances, no saved progress. Back to the start you go, my lad. With only gradual changes in direction available it’s a game that requires forethought as well as agility.

Walking dead
While there's a decent selection of weapons – including a chainsaw, a shotgun and even an Alsatian dog – ammunition is a scarcity and supply dumps are often beyond reach due to that limited ability to change direction. Thanks to the sombre, fog-blanketed landscape and the blood-curdling gurgles from the zombies, gameplay is nothing if not atmospheric. The controls are excellent and you can happily ignore the in-game purchase options without limiting your enjoyment.
Modern Combat 4: Zero Hour

OK, the plot is a load of macho cobblers, the dialogue reads like it was written by someone who is not a native English speaker, and you need plenty of space (1.8GB) and money (a fiver), but MH4:ZH still delivers an impressive dollop of full-on FPS action but on your tablet rather than your Xbox or PlayStation. Graphics and sound are both very impressive, though the more power your device has and the higher its screen’s pixel density, the better it will play and look.
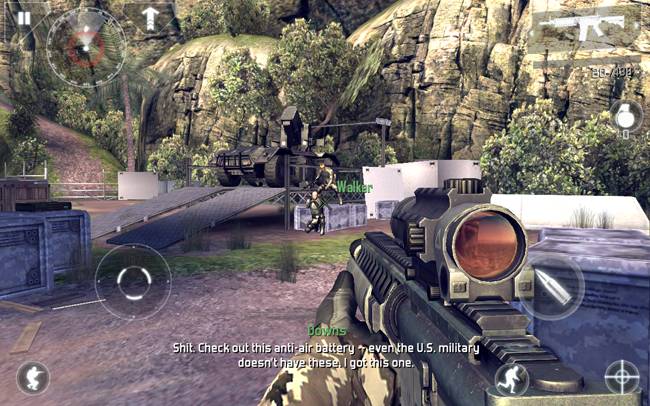
Do jarheads really talk like this?
The controls aren’t what I’d call perfect but you can move them around on the screen until you find a layout that is at least useable in the heat of combat. The single-player campaign is one of the best that Gameloft has delivered recently and sees you flip between US Special Forces and the inevitable terrorist opposition, sometimes playing both sides of the same firefight. At least the latter are home grown libertarian-types rather than stereotypical Arabs or Russians. Yes it’s sound and fury signifying nothing, but it’s very impressive sound and fury.
