This article is more than 1 year old
Four ways the Guardian could have protected Snowden – by THE NSA
Spooks' own advice lays out exactly how this crypto wypto hypto thing works
3. How to shift the data securely
It's time for your source to package up the goods to leak: your contact can either use your public key to asymmetrically encrypt the files using PGP or if you've somehow agreed upon a key (typically generated from a pass-phrase) that is utterly secret between you two, then consider symmetric encryption using AES-256.
If this symmetric key falls into the wrong hands, then the jig is up, whereas in asymmetric encryption, you just have to be responsible for your own private key. Having said that, using AES-256 to encrypt your leaked data (once you have it) on removable storage, perhaps steganographically inside a video or TrueCrypt volume, is essential.
Encrypting files, once they've been archived into a zip or tarball for convenience's sake, is just a simple command line away. For symmetric, try:
gpg --output totallyinnocent.txt --symmetric leakedsecrets.pdf
...or for asymmetrically use:
gpg --output totallyinnocent.txt --encrypt --hidden-recipient Friend leakedsecrets.pdf
In the latter case, the source must have added the public key for Friend (that's you) using gpg --import. GnuPG is completely documented.
Of course, you'll need to exchange public keys. To avoid having to rely on encrypted instant messaging systems (such as OTR), publish your public key online, in the open. The first communication you may get from your leaker is an encrypted message from a throwaway email account from a Wi-Fi hotspot, and unfortunately such data is likely to set off triggers within the spooks' internet surveillance systems. The chase will be on immediately.
Once the leaker has encrypted her data, it's time to transfer it. Don't use email. Don't even consider uploading the file to a server across the open web, even if the data is encrypted: with the global internet dragnet in operation, you do not want to accidentally reveal your source by allowing spooks to realise the association between the two of you. (Life is made easier if your source outs himself, like Edward Snowden did, but then life hasn't been easy for him since.)
So consider using Tor, first backed by the US Navy for secure communications and then developed by the Electronic Frontier Foundation (EFF) and others. This is a system that routes connections through a mesh of computers joined up to the Tor network: your connection goes into an entry node, through a randomly selected path, jumping from machine to machine, until it reaches an exit node, which connects to the outside world. The exact path taken is decided by the user's software and cryptographically shielded to prevent someone from tracing you back through the network.
The computer you eventually connect to outside the Tor network will only see a connection from the exit node – and, yes, this node can snaffle your network traffic so that's why we encrypt everything just in case someone compromised it (use a secure VPN if you wish, but that's beyond the scope of this piece).
How Tor works is best described with illustrations, such as the one below from the EFF, which has an excellent guide here.
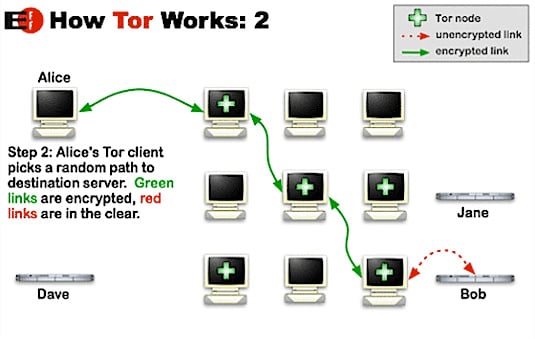
Unfortunately, as noted computer security researcher The Grugq pointed out, the NSA and GCHQ will have all the entry and exit points of Tor covered:
The financial cost of compromising the Tor network is not even a rounding error in a nation state budget. It is the equivalent of a portion of the change found in the couch. Further more, Tor is not new. It isn’t as if nation state level adversaries just woke up last week, “holy shit, this Tor thing! We better get on that!”
The trick, in El Reg's opinion, is to get the data transferred before the spooks put a crack team on you and your mole to swipe the keys or otherwise prevent the leak. So, if you're persevering, set up a hidden service, which allows your source to securely connect to your server across the Tor mesh. See, no need to fly a data mule through Heathrow.
4. Using hidden services
Take a clean, secured new PC and hook it up to the internet far away from your other networks; run an SSL protected web or FTPS server and allow your leaker to anonymously upload files to it, effectively creating your own personal drop box.
Agree on a time and date to do this, and pull the plug once the deed is done. And do this after the source has fled to a country without a US extradition treaty, such as Ecuador.
Then you can transfer the encrypted data, via removable media, to your clean not-networked VM to decrypt with the private key you've kept away from everything. Publish the juicy details before someone can slap an injunction on you, officials turn up and demand some computers are smashed up, or armies of state-sponsored hackers try to raid your setup for all the data you hold.
So that's your air gap. Those are the hoops you need to jump through. You may as well hide some secret encrypted data in a video, put it on a DVD, and post it first class.
And, lest your humble hack hasn't made his point strong enough, you're up against a nation state, not some credit-card stealing hacker; even if you don't believe spies can record conversations in rooms using lasers pointed at windows, they have resources.
As The Grugq concluded after the Snowden scandal broke, you're dealing with plenty of unknowns:
Practicing effective counterintelligence on the internet is an extremely difficult process and requires planning, evaluating options, capital investment in hardware, and a clear goal in mind. If you just want to “stay anonymous from the NSA”, or whomever … good luck with that. My advice? Pick different adversaries.
Speaking of which, let's not forget the tech giants holding all our data for years. The big cloud providers know everything about us, although Google and its fellows insist that staff access to netizens' personal data is highly restricted.
As one UK government security staffer complained to El Reg even before the NSA PRISM firestorm kicked off: "You would not believe the hoops we have to jump through to access an email, all the legal paperwork that needs completing, when Google has everyone on file and no one blinks an eye." ®
