This article is more than 1 year old
What happens on G-Cloud stays on G-Cloud
How to use SharePoint online and keep IL3 information secure
With the advent of the G-Cloud and the introduction of the UK Government’s Cloud First initiative in May 2013, the impetus to use the cloud to carry out daily tasks and plans has never been greater.
Historically government departments and the wider public sector have shied away from the cloud because of concerns about storing and sharing highly sensitive personal data.
In response to this, the Government has devised a process to assess security risk, dividing it into grades known as impact levels (ILs):
Impact level 1: Unclassified
Impact level 2: Protect
Impact level 3: Restricted
Impact level 4: Confidential
Impact level 5: Secret
Impact level 6: Top secret
All government departments must assess the impact level of the data they hold and share with third parties. To get onto the G-Cloud framework and CloudStore IT suppliers must ensure their products and services are rated for the appropriate impact level.
Drawing up the list
Available cloud options were reviewed for providing national sharing of IL3 level information internally and to approved external parties. There could be no compromise of security, data integrity and confidentiality.
From the initial research, it became clear that a SharePoint Online Extranet was the most appropriate solution for sharing and accessing information up to impact level 2. However, the organisation also needed to share IL3 information.
After searching the G-Cloud framework for security-accredited companies, the organisation commissioned an accredited Microsoft Partner to set up a portal that would share IL2 information through a Microsoft SharePoint Online Extranet and a Windows Azure WCF service.
The portal also enabled the organisation to connect to the IL3 internally, keeping the most sensitive data within the internal firewalls while allowing external access to it.
The shopping basket
The following components were required to build the cloud-based system: Office 365/SharePoint Online for IL2 data; the Windows Azure-based WCF service for the connectivity backbone; and an internal SQL Server for IL3 data.
The solution gives the government organisation a secure mechanism for sharing IL2 data and to easily connecting to IL3 data. Furthermore it provides significant cost savings both in the initial setup and the on-going operational expenditure, thanks to the cost-effective Microsoft G-Cloud based offerings.
So how does it all work? The diagram illustrates the high-level flow of data through the various components, both when retrieving and submitting data.
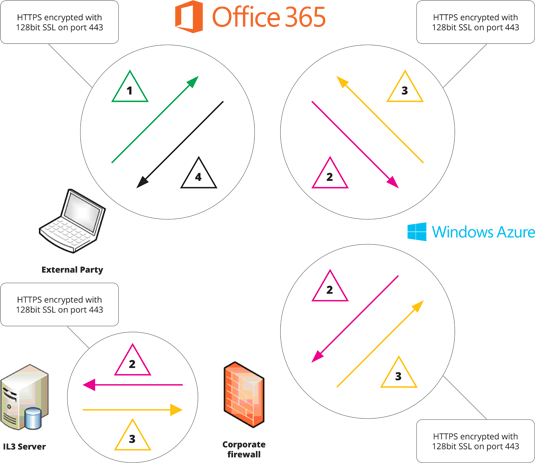
Viewing data
1. The user opens the browser, navigates to the SharePoint Online site and authenticates with Office 365 username and password.
2. SharePoint Online Business Connectivity Service requests IL2 data from on-premise SQL Server database using an Azure WCF service and the OData protocol and authenticates using credentials stored in the SharePoint Online Secure Store service.
3. Only IL2 data is passed from the SQL Server database to SharePoint Online Business Connectivity Service for processing
4. The SharePoint page is rendered to user with the appropriate data shown
Submitting data
1. The user opens the browser, navigates to SharePoint Online site, authenticates with Office 365 username and password and submits a form containing IL2 data.
2. SharePoint Online Business Connectivity Service submits the IL2 data to the on-premise SQL Server database using an Azure WCF service and the OData protocol and authenticates using credentials stored in the SharePoint Online Secure Store service.
3. IL2 data is linked to the related IL3 data internally and feedback is passed back to user.
4. SharePoint page is rendered to user with appropriate feedback.
The result
By using SharePoint Online and the Windows Azure platform, the organisation has been able to share highly sensitive data with approved external parties without compromising IL3 data security or its own corporate firewall. ®
This article was produced in association with CoreGB, a London SharePoint consultancy. Eamon McGann is operations and technical director and Phillippa Ritchie is head of consulting and design.
