This article is more than 1 year old
Prince of Persia: Baggy trousers and curvy swords
Jordan Mechner’s animation classic
Turban sprawl
Such complex character control was essentially unheard of at the time, and was as much a revelation as the accompanying animation. It’s certainly held with fond regard in gaming circles, as this well-crafted tribute video shows:
Following the initial Apple II version, releases for other platforms featured further spruced-up, re-worked visuals. Indeed, it would appear that Mechner had managed to become the prince of his own small Persian empire, employing multitudinous developers and publishers to branch out across the various platforms of the time. Console ports contained redesigned levels, and a sequel, though generally well-received, put more emphasis on combat – a shame in some ways, since this was never the title’s strongest card.
Whatever version you were enjoying, the convoluted puzzles – some were finely set up, elaborate brain-teasers – set the title apart from other platform games. Without the password system for returning later, one would soon have tired of endlessly repeating levels, but with it Prince of Persia became a hugely addictive experience. Indeed, thoughts of how to complete each incrementally more difficult level became all consuming – the hallmark of a truly classic game.
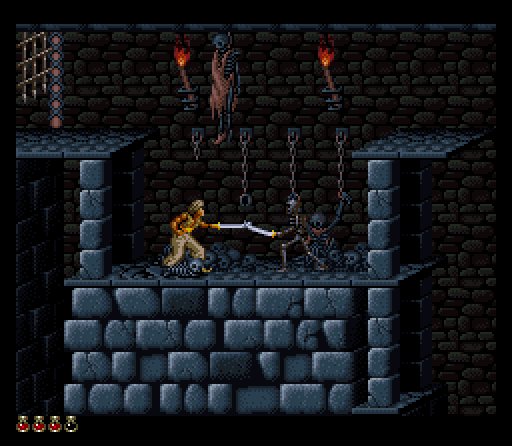
The Super Nintendo brought a more arcade feel
After the first wave of Prince of Persia conversions and sequels, Mechner took his rotoscoping and movie-making ambitions a step further, working on The Last Express, a game that took over five years and millions of dollars to develop. Its release received critical acclaim, but the title was commercially unsuccessful due to publishers Brøderbund and SoftBank going down the pan at just the wrong time. It remained one of video-gaming’s long-lost classics, though gladly an iOS conversion released last year brought it back from the grave, albeit with slightly inconvenient controls.
The Prince of Persia franchise has been re-hashed, re-worked and re-released for many platforms over the years, making the jump to Prince of Persia 3D as early as 1999. Unfortunately, that title was pretty average, just like so many early 3D platformers, where designers hadn’t quite worked out how to handle the tricky third dimension.

Sands of Time brought good, true 3D Prince of Persia gaming
It would be a few years’ wait until 2003’s The Sands of Time stormed onto PC, Xbox, Gamecube and PS2. This groundbreaking title, along with sequels Warrior Within and The Two Thrones, did far better justice to the notion of a 3D Prince, and was clearly much more than just a link to one of video-gaming's seminal moments. Well-crafted acrobatic moves and complex combat sequences combined with interesting extras like the ability to re-wind time, and the assistance of Farah, a non-playable character, who helps our hero to solve puzzles.
In 2010, Forgotten Sands reprised the storyline of these excellent new 3D games, and all three previous titles were given high definition re-releases to coincide with the release of the movie version. Thus it was vaguely inevitable that while Prince of Persia had been given some very worthy 21st Century gaming updates, the series still wasn’t immune to the damning world of game-to-film conversions. Yes, they drafted in Ben Kingsley and that young bloke from Donnie Darko, but the motion picture was still pretty poor.

Belly dance: Warrior Within
Still, it does remain the highest grossing game adaptation yet, so what do I know?
Jordan Mechner is obviously a multi-talented guy, with inclinations towards all sorts of media aspirations. Hopefully, he’ll find a few more gaming gems up his finely animated sleeve at some point in the future. Prince of Persia is a slice of gaming heritage that deserves to live on for a few more decades. ®
Jordan Mechner’s 6502 assembly code for the first Prince of Persia can be viewed on GitHub.
Developer Jordan Mechner
Publisher Brøderbund (other publishers handled certain ports)
Platforms Pretty much all of them
