This article is more than 1 year old
Black hat greed reducing software vulnerability report rate
Zero-day market temptation: Cash out or collaborate?
RSA 2013 HP has kicked off the round of reports that accompany each RSA conference with its analysis of security vulnerabilities, and has revealed that although the overall trend is positive, the growing market for zero-day flaws is reducing the number of the most serious problems that are disclosed.
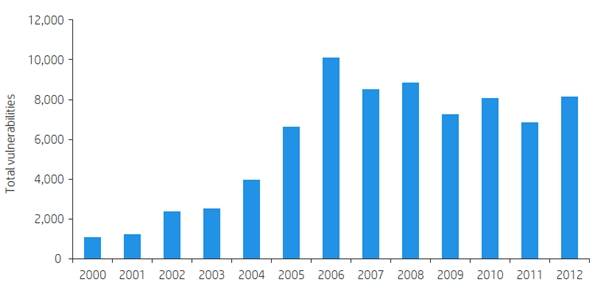
The long-term trend looks pretty good, but...
The number of software vulnerabilities has continued its overall downward trend from its 2006 peak, but while the numbers of the most critical threats hasn't fallen much, HP researchers have seen a reduction in the number of serious vulnerabilities that are actually reported. HP attributes that slippage to the growing market for vulnerability data.
"We think a lot of these vulnerabilities are being sold in the black market or the grey one," Mark Painter, marketing manager for Fortify HP enterprise security, told The Register.
"The growth of the grey market and the worth of vulnerabilities in dollars must have a reducing effect on the number of public disclosures that we see," Painter told us. "Those dollars are there, and anything that goes down [the grey channel] doesn't become public."
Four of the six most common vulnerabilities are aimed primarily or solely at web applications: SQL injection, cross-site scripting, cross-site request forgery, and remote file inclusion. Together these account for 4 per cent of the total.
On the mobile front, the HP team tested a very small sample of 70 apps and found a host of problems. Over 37 per cent of applications had passwords that could be beaten using basic methods (such as Apple's latest passcode-bypass woes), and 77 per cent had information-leakage flaws.
There was a relatively low rate for XSS vulnerabilities in mobile, with an unlucky 13 per cent of mobile apps at risk, but the data showed a worrying preponderance of financial and database management apps in the sample.
Elsewhere, HP reported a huge increase in the number of SCADA (supervisory control and data acquisition) vulnerabilities detected, the numbers of which have risen 68 per cent over the last five years. This likely reflects that people are more actively looking for such things post-Stuxnet, rather than any inherent instability in SCADA code. ®
