This article is more than 1 year old
Review: Britain's 4G smartphones
Nine handsets, one network - is it time at last to invest in LTE?
Samsung Galaxy Note II
If you can get past the size - not easy I grant you; I waver between thinking it’s not that massive to guffawing at the sheer absurdity of it - then the Note II is a technological beast of a device in all ways. The whopping 5.6-inch, 1280 x 720 AMOLED screen makes web browsing and gaming a visual feast while the stylus offers a host of handy extra functions.

Of course the real value of the Note as a 4G device is that vast, removable battery. This is the only phone here that can actually be used consistently on a 4G network and not have you checking for the nearest power socket in a cold sweat every half an hour. It’s near-tablet dimensions also go some way towards justifying the whole 4G idea - you can do so much with a Note that maybe, just maybe screaming data speeds are worth paying for after all.
Samsung Galaxy S III
All the ingredients that have made the S III a worldwide sales hit are present and correct in the LTE version, though sadly so is the standard 2100mAh battery. Since the S III already has a removable battery it would hardly have been an engineering challenge for Samsung to have installed a larger one. But as the S III already lasts longer on a charge than any other handset here bar the Note II I can’t spank it too hard for that failing.
With a vivid 4.8-inch, 1280 x 720 AMOLED screen and a heavily modified version of Android Jelly Bean with all manner of extra goodies built in, the S II is a lot of smartphone for the money. It’s powerful too thanks to a 1.4GHz quad-core processor. I’ve heard tell that this i9305 model has 2GB of Ram, but mine only seemed to have the usual 1GB. With a Micro SD slot to back up the 16GB of built-in storage, it’s not hard to understand why the world and his wife wants one of these things - and why it has put the wind up Apple.
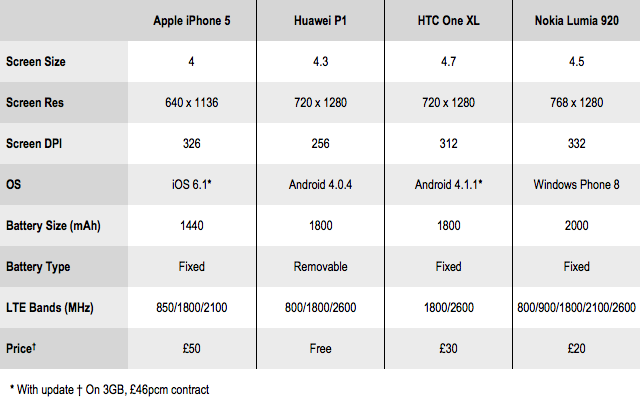
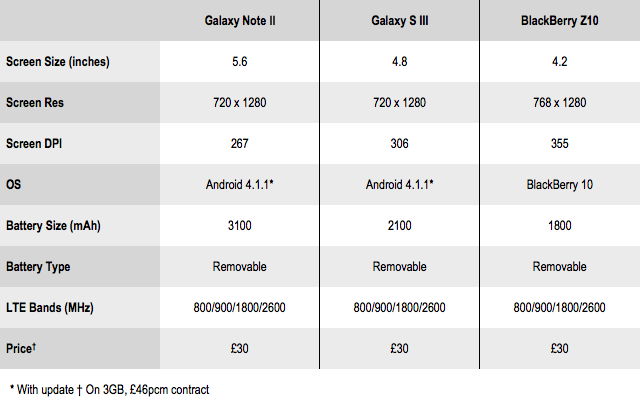
The UK's 4G phones at a glance