This article is more than 1 year old
Online crims are getting away with it down under
Just eight per cent of perps charged, five per cent of attacks come from foreign powers
Law enforcement agencies charged with investigating online crime might actually be sitting at their desks gorging on donuts in Australia, if the nation's Computer Emergency Response Team' survey of stakeholders is to be trusted.
The results of that survey, published today, states that “Out of those respondents who did report a cyber security incident to law enforcement, 33% stated that it was their understanding the incident was not investigated … while 8% of matters referred to law enforcement were reported to have resulted in a person being charged.”
Vulture South takes security surveys with the largest available salt crystals, but CERT Australia's effort is worth more consideration than the endless torrent of vendor-commissioned security surveys inasmuch as it has less need to keep us all scared and therefore primed to buy more stuff. That the survey was “conducted in partnership with the Centre for Internet Safety at the University of Canberra” also gives us more comfort, although the small sample – “of the almost 450 organisations contacted, responses were received from 255” - leaves the study far from representative.
That the CERT “works with the Australian business sector – primarily the owners and operators of systems of national interest” further skews the sample.
If you can still stomach the study after those caveats, it may perturb to know that the report couches its findings in positive terms.
For example, it notes that “More than 90% of respondents reported using antivirus software, spam filters, and firewalls.” How many “operators of systems of national interest do without is not revealed. What is known is that “More than 80% also reported using access control and virtual private networks,” again leaving a few without.
“Almost 60%” run intrusion detection systems (IDS).
Another eyebrow-raiser is the finding that “less than 50% of respondents have plans in place for the management of removable computer media, such as USB memory drives” and 84% practice “user access management.” The latter response makes us uneasy about another element of the study's methodology, namely the anonymised 24-question online survey, as it seems to your correspondent easy to respond negatively to a query about “user access management” given the term does not have wide currency.
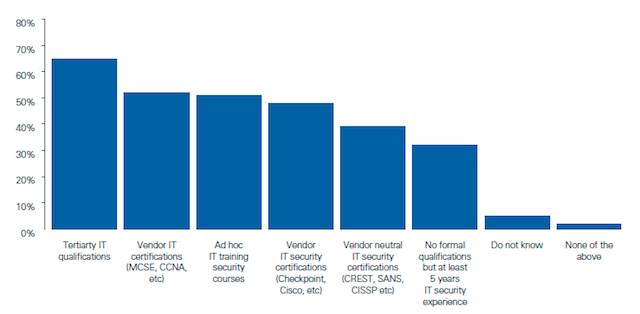
65% of participating organisations had IT security staff with tertiary level IT qualifications.
Another interesting finding, graphed above, is that “Almost 35% of participating organisations had IT security staff with no formal training, although most of these staff had more than five years working in the IT security industry.”
Just 22 per cent of respondents 'fessed up to a security incident during 2012, a number CERT Australia puts down to an unwillingness to admit to attacks. A further nine per cent admitted ignorance on the matter. Theft of a device was the most common incident reported.
Motives for attacks were “illicit financial gain (15%), hactivism (9%), using the system for further attacks (9%), using the system for personal use (6%), being from a foreign government (5%), personal grievance (5%), and being a competitor (4%).”
The full report is available here (PDF). ®
