This article is more than 1 year old
Nintendo Wii U Review
'Asymmetric gameplay', anyone?
Paddle out
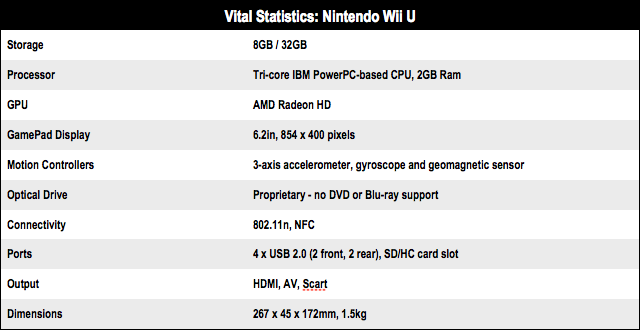
Storage solved, it’s on to the real reason we’re here: the GamePad. The presence of an easy to use tablet in your lounge will be a thrill for those who have yet to experience the joys of, say, an iPad.
The GamePad’s screen at 854 x 480 and 158ppi, while not as sharp as the iPad, still looks bright, vibrant and near enough to HD to mean you won’t miss it. It comes with touchscreen, stylus, camera, microphone, gyroscope and accelerometer. It’s also surprisingly light and ergonomically designed so that even my longest stints haven’t led to aches or finger cramping.

Birds of play
Quickly glancing from TV to GamePad, depending on the requirement of its games, soon becomes second nature. And I’ve yet to lose the buzz of swapping and changing the action from TV to GamePad to carry on playing even when the TV is unavailable.
Once a game is running on the GamePad play is lag free and the resulting visual down-scaling barely noticeable. However, a little experimentation revealed the GamePad’s roaming range is not as great as I’d hoped.
Moving about 5m away from the Wii U is enough to prompt the ‘corruption interrupted’ screen which means, sadly, that’s there’s no Mario while sat on the loo for me – a blessing no doubt. It did reach my bedroom though – Batman in bed anyone? – but don’t be surprised if its signal won’t permeate every room of your house.
Battery life is a concern too; it takes about three hours of play to drain, so you’ll have to plug the GamePad in to keep playing. Should you not happen to have a wall socket located handily next to your sofa of choice that’ll be an issue, plus the GamePad sure doesn’t look as pretty with wires sticking out of it.

The processing power of the Wii U is a further point of discussion. Hard tech facts like it has an IBM Power multi-core processor, 2GBs of DDR3 SDRAM (1GB to the OS and 1GB to the games), an AMD Radeon-based High Definition GPU, don’t really say much to the average consumer.