This article is more than 1 year old
Samsung Galaxy Note 2 review
The most complete digital communications device known to man?
Bonus points
Being a Samsung device Android is here overlaid with TouchWiz but I’m prepared to forgive it this foible even if it’s a bit like painting a moustache on Rossetti’s Beata Beatrix. Yet, with all the extra functionality built into the Note 2, there is at least a solid reason for messing around with Google’s mobile OS beyond the simply aesthetic or bloody minded.
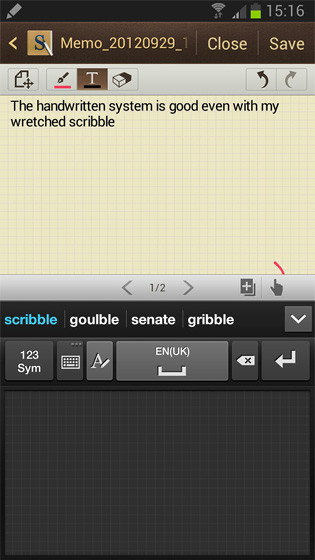
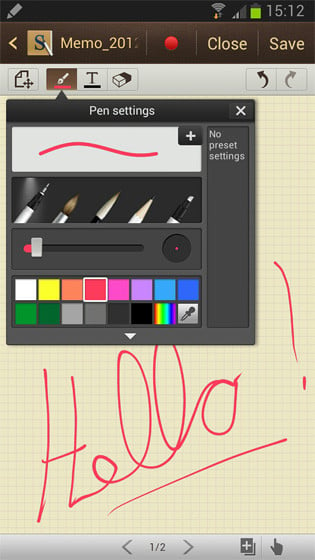
Memo options: handwriting recognition and note taking
Make no mistake, Samsung has added a truly bewildering – perhaps even excessive – amount of extra functionality the Note 2. Gesture commands, floating video screens and context-aware home pages. There's also a funky auto-rotate feature that uses the webcam to judge the angle of a line between your eyes relative to the device, which is handy if you are using the Note while lying down. The list just goes on.
Lest we forget the S Pen which is the Galaxy Note 2’s party trick. With this stylus, you can write, sketch, doodle and grab the screen in all manner of useful ways. Damn shame though that screen video record function seems to have bitten the dust between Samsung’s video guide and the Note 2 hitting the shelves.
The new Pen has an oblong rather than round profile making it easier to hold and easier to slot into its bay the right way. There's no lanyard to connect S Pen to Note but if it detects you walking away without replacing the stylus it will start beeping which is useful.
The Note’s screen can sense the pen before it touches down, thanks to a feature called Air View. Hover over a gallery, video or e-mail with the stylus and a preview of the file opens. I have to admit this is not a feature I've been crying out for on a mobile phone but it is pretty cool. Handwriting recognition is also much improved over the original Note.