This article is more than 1 year old
AMD and Intel extreme desktop CPU workout
Feel the burn
Core decisions
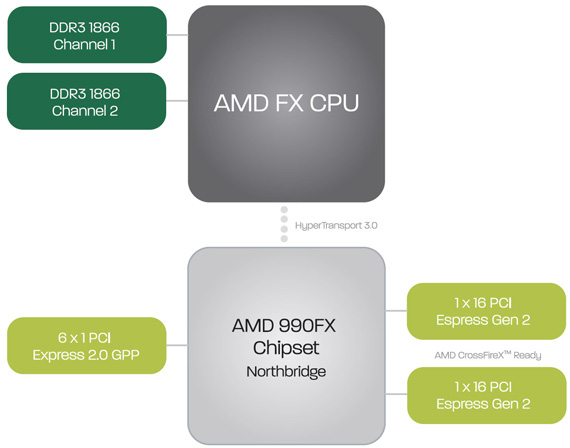
Indeed, it had been a very long wait for anything totally new to come out of AMD’s CPU camp but its Bulldozer architecture was built from scratch and finally arrived in October 2011 – its totally new modular design raised considerable interest. In essence, each module is a dual-core CPU with each core having its own 16KB of L1 cache and 2MB of L2 shared between each module while 8MB of L3 cache is shared between all the cores in the die.
AMD Bulldozer architecture block diagram
All this combined makes the Bulldozer a big chip, with a die size of 315 mm² and a 1.2 billion transistor count. Bulldozer also uses the existing AM3+socket, unlike Intel’s Sandy Bridge E that requires new components. The FX-8150 has four of these Bulldozer modules and therefore is a 8-core chip with a core clock of 3.6 GHz, which rises up to 4.2GHz with AMD’s Turbo technology.
The fact that it doesn’t have any competition from AMD in the high-end performance processor market has made Intel pretty complacent, for example both the Core i7-3960X and Core i7 3930K aren’t quite what nature intended them to be. In truth, they are both eight-core chips but have two cores disabled simply because Intel doesn’t feel the need to have an eight-core chip in this market space. Besides, if AMD had a complete change of heart and launched some fire breathing chip, then all Intel has to do is to enable those redundant cores and launch a new range to combat it.
Intel X79 Express chipset block diagram
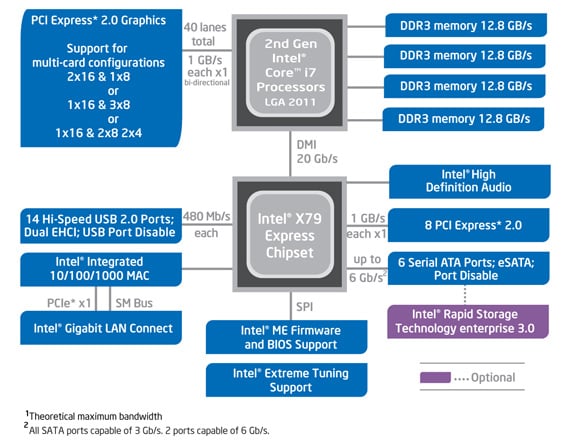
So for now, just like the Core i7-3960X Extreme Edition, the Core i7 3930K is a six-core Sandy Bridge E processor with hyper threading. In effect, the latter delivers 12 threaded chip built on a 32nm process. The 3930K is a 100MHz slower than the 3960X, clocked at 3.2GHz (3.8GHz with Turbo) with 12MB of Intel L3 Smart Cache and it supports quad memory channels.
