This article is more than 1 year old
WTF is... Intel's Ivy Bridge
Inside Core i's third generation
Graphics
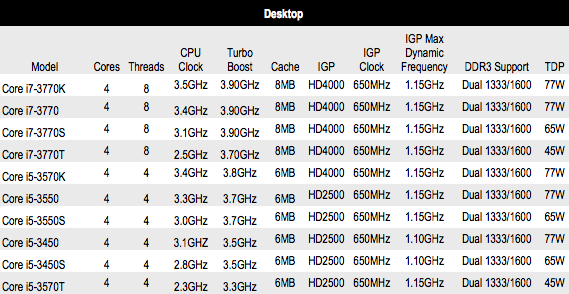
Smaller transistors require less switching power, reduced further by the Tri-Gate design, which manifests itself as a lower power consumption. Using the Core i7-2700K as an example again, its TDP (Thermal Design Power) is 95W, which the i7-3770K, at the same clock frequency, knocks down to 77W.
While lowering the power consumption for the desktop chip is good, it’s really going to make a real difference in mobile, battery powered platforms.
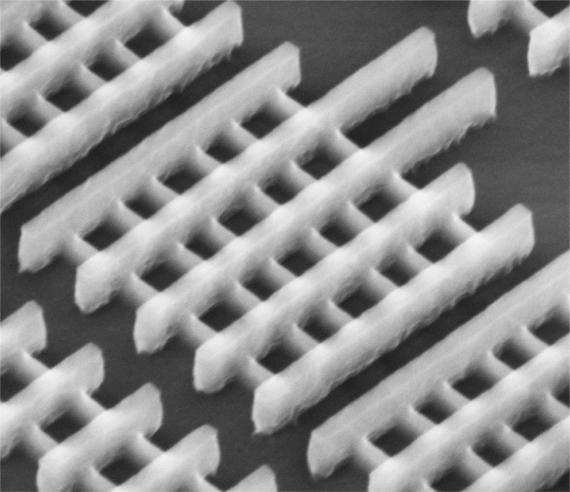
Shreddies style chips: Intel's 22nm transistors
The most significant change within Ivy Bridge's architecture is its integrated graphics processor (IGP). Probably the most important upgrade: the IGP now supports DirectX 11. Yes, it’s been a long time coming, but it’s here at last, allowing Intel's graphics to deliver the features defined by the latest incarnation of Microsoft's Windows gaming sub-system.
There are two versions of the IGP. First, there's the HD 4000, which will feature in the high-end Ivy Bridge chips. It has 16 shader units and a core speed of up to 1.15GHz. Although the core is capable of running at 1.35GHz, this higher speed will only be available to mobile CPUs.
The second Ivy Bridge IGP is the HD 2500, aimed at the mainstream market. It has a core speed of 1.15GHz too, but with just six shader units.
Both IGPs are set to run at 650MHz, but can reach the higher speeds if the need arises. Again, this is all in the name of energy preservation.
Intel has also added is hardware tessellation to the IGP, which speeds the process of breaking large areas of an image into small ones which can be textured, lit and, where possible, duplicated. It all helps the IGPs push out more pixels per second.
Intel's Wireless Display technology - think using Wi-Fi in place of an HDMI cable - is now at version 3.0, which has lower latency than before and supports two screens, thanks to the IGP's pixel-processing capabilities. The new IGP also is able to support three displays instead of two through wired links.
Intel has taken the opportunity to enhance its processors' security adding a Digital Random Number Generator (DRNG), a high speed number generator to churn out cryptographic keys quickly and less predictably than basic, pseudo-random number generators in software.