This article is more than 1 year old
Scientists refine smart self-assembling building blocks
'Smart sand' replication algorithms proven
Scientists at the Massachusetts Institute of Technology say they have shown how to code smart substances that can automatically copy an object and reproduce it.
The team from MIT's Distributed Robotics Laboratory have developed a testable algorithm that uses interlinking smart systems – in this case, "smart pebbles." These are cubes one centimeter across that contain four magnets and a basic processor, which map out the shape of objects they surround and communicate it to each other.
Once the shape of the object has been identified, the position of the smart cubes is remembered and used to replicate more copies of the original. The eventual goal is to engineer "smart sand," a series of tiny, intelligent units that can be used not only to provide copies of objects, but also to form and reform into a series of specific tools.
Student Kyle Gilpin, who worked on the project, said that the current smart pebbles are limited by engineering. For example, they only work in two dimensions at the moment, because "there just wasn't room for two more magnets."
The processing units themselves can also only run 32KB of program code with around 2KB of memory. But as engineering techniques improve, the possibilities become more interesting.
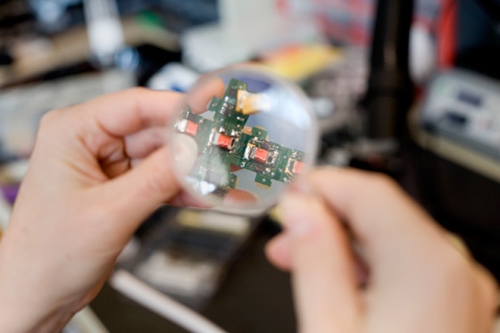
Robot pebbles under construction
Robert Wood, an associate professor of electrical engineering at Harvard University, said this was certainly possible. "Take the core functionalities of their pebbles," says Wood, director of Harvard's Microrobotics Laboratory. "They have the ability to latch onto their neighbors; they have the ability to talk to their neighbors; they have the ability to do some computation. Those are all things that are certainly feasible to think about doing in smaller packages.”
Such devices are certainly getting smaller. When one current El Reg hack first wrote about such units five years ago, they were 4.4cm across. Assuming a steady rate of shrinkage, we might have smart sand within the next 50 years.
The full work by MIT's team will be presented at the IEEE International Conference on Robotics and Automation next month. ®
