This article is more than 1 year old
Behold! Or rather, don't: Bendy see-through DRAM
You like windows, you like bendy things, you like memory
Boffins at Rice uni in the States have devised bendy transparent memory chips using pure silicon crystals.
James Tour, a polymath chemist at the university working at the Tour Lab - he is also a professor of mechanical engineering and materials science and of computer science, as well as Rice’s T.T. and W.F. Chao Chair in Chemistry, revealed the see-through memory chip an an American Chemical Society meeting in San Diego.
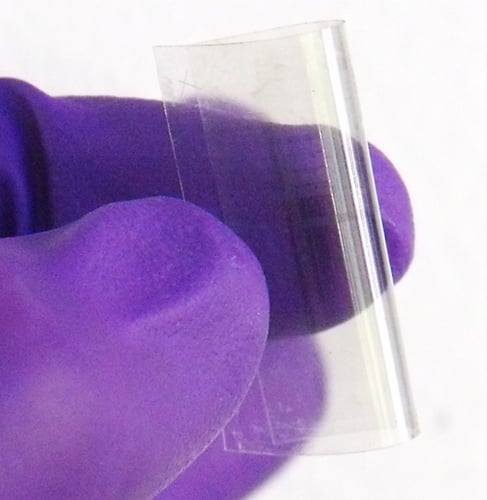
Transparent flexible RAM (Rice University)
Tour said: “Generally, you can’t see a bit of memory, because it’s too small [and] silicon itself is not transparent. If the density of the circuits is high enough, you’re going to see it.”
A 2010 discovery showed that "pushing a strong charge through standard silicon oxide, an insulator widely used in electronics, forms channels of pure silicon crystals less than 5 nanometers wide. The initial voltage appears to strip oxygen atoms from the silicon oxide; lesser charges then repeatedly break and reconnect the circuit and turn it into nonvolatile memory. A smaller signal can be used to poll the memory state without altering it."
The Tour Lab has made a 2-terminal prototype device stackable in a 3D config attached to memory The Rice lab has since developed a working two-terminal memory device that can be stacked in a three-dimensional configuration attachable to a flexible substrate, giving us a bendy transparent memory.
We might end up wearing our memory devices. ®
