This article is more than 1 year old
Infinity Blade II
In need of a quick slash?
iGamer I liked the original Infinity Blade when it arrived just over a year ago, but it seemed to fall short of classic status due to the repetitive nature of the combat, the rigidly linear exploration and threadbare fantasy storyline.
This sequel does try to add a bit more variety to the formula, although I still found the continuous conveyor belt of demonic foes a tad tedious at times.
I was also a little miffed at the price increase: £4.99, compared to £3.99 for the original. And I’m no great fan of games that tempt you with in-app purchases for weapons and other items either – although, to be fair, you can still get by perfectly well without having to cough up extra cash for the Super Sword Of Thumping+3.

Blinded by the light: optical effects abound in IB II
The original Infinity Blade looked wonderful, and Infinity Blade II goes even further thanks to the A5 processor in the latest iPhone and iPad.
Developer Chair has really gone to town with the lighting effects, with endless shafts of light streaming through foliage and epic vistas with castles perched on craggy mountaintops.
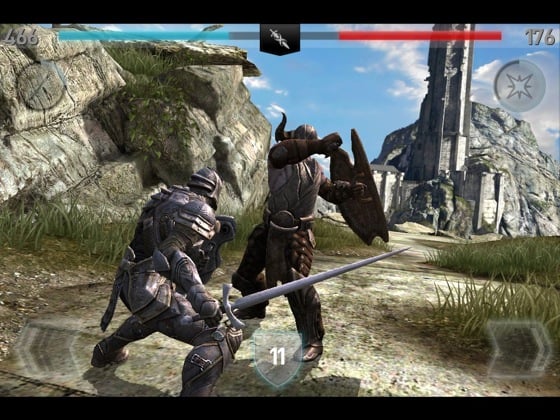
The swipe'n'slash combat remains - but with a few new twists
In fact, it got so carried away with the lens-flare effects that there were times when I felt I needed sunglasses to go into combat.
And why is there lens flare anyway? Do games developers only see the real world through a camera's optics? My eyes certainly don't bring their own Photoshop filters with them.

You can now use two-handed hardware
The storyline follows straight on from the original game. You've wrested control of the mighty Infinity Blade sword from the God King and now you're heading off in search of the mysterious Worker of Secrets for some reason that I didn’t entirely understand.
Fortunately, there’s a tie-in paperback advertised within the game to shed some light on the finer details of the plot. And a soundtrack album too.
Ker-ching!
