This article is more than 1 year old
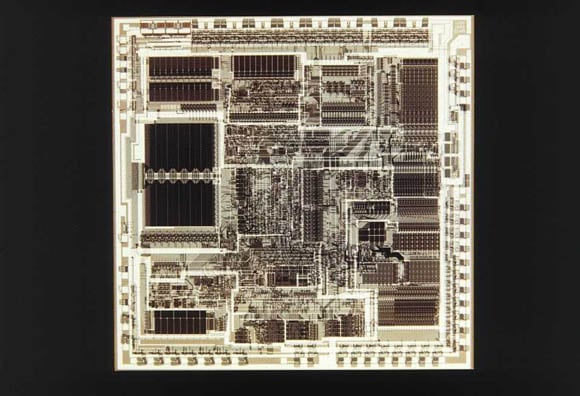
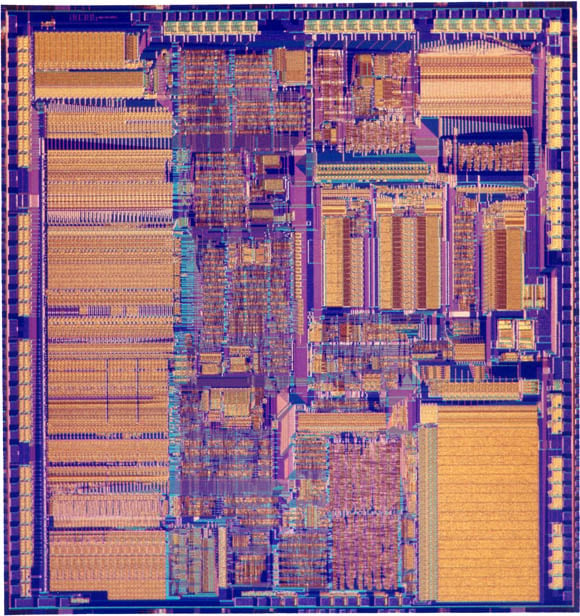
Happy 40th birthday, Intel 4004!
The first of the bricks that built the IT world
Playing catch-up with Motorola
The Pentium's superscalar nature was playing catch-up with Motorola, which had offered superscalar chips for some time. According to Pawloski, the reason that Intel hadn't moved to a superscalar architecture earlier was that the jump from 16-bit to 32-bit mode, while making sure that all existing 16-bit code ran swimmingly, was enough to keep Intel's engineering team occupied.
"At some point in time you don't want to bite off too much," he told us, "otherwise you're going to run into so many problems."
And problems did dog the P5, at least at first. There was, for example, an FPU bug that was the butt of many a joke, and the early 0.8-micron parts were roundly criticised for their toastiness – a problem that dissipated as the P5 architecture was moved to smaller processes and lower voltages.
Although the P5 had introduced superscalar architecture to the Intel line, Pawlowski contends that it was P6 design effort, begun in the early 1990s, that was the greatest achievement of that period.
"I contend that the success of that part," he said, "was because it brought in people that hadn't built the traditional lineage of x86 components" – architects such as Bob Colwell, Dave Papworth, and Mike Fetterman. "Those guys really made that machine," Pawlowski told us.
"There was a big argument between the Pentium and the P6 group, because the Pentium group felt that, 'Hey, that's probably not going to work, that's a huge step, x86 compatibility is going to really be tough'," he recalls.
"One of the reasons that I was brought into the program," he said, "was because I built PCs. In a lot of cases the individuals that were working in that program – because they were non-Intel or they hadn't been exposed to the PC side of the market – well, their feeling was 'We don't have to worry about being compatible, we're doing something new and different'."
That argument didn't cut it. "At the end of the day we said, 'You're going to be a PC, so you better get used to it'," he told us. "So what we did, in the group I was in, was we brought PC compatibility to the part." And x86 compatibility has remained a core tenet of Intel's chip development since.
Well, there is that little thing called the Itanium, but we digress.