This article is more than 1 year old
The Register Guide on how to stay anonymous (part 2)
The Evercookie: Like trying to kill Steven Seagal
Prevention is better than the cure
None of these tools however prevent the LSOs from being created in the first place. This is because in order to do so, you have to prevent the add-ins from running. For that you need something like QuickJava.
QuickJava allows you to build whitelists and/or blacklists to prevent Java, JavaScript, images or Flash from loading on a web page. It loads an icon in the status bar to show what has been run on the page, and gives you the ability to disable them with a single click.
QuickJava is a fairly high maintenance plug-in; it requires you to maintain your own lists, but it is far less intrusive than the alternative.
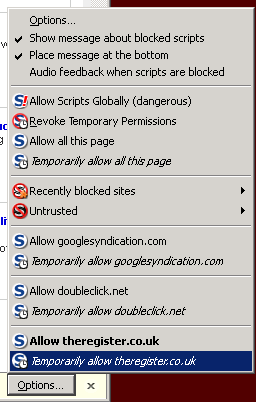
The alternative, of course, is NoScript. NoScript's approach to browser security is to nuke a site from orbit. It's the only way to be sure.
NoScript does not allow any scripts to run by default. You must allow each domain from which you want to approve scripts to run. Any third-party tracking elements – any script, or application that uses a (non-whitelisted) domain name – will have to be manually enabled. Domains can be whitelisted permanently or temporarily, and it can be further locked down to provide absolutely complete preventative security. It even includes clickjacking protection.
And yet, it moves
All of the above presupposes things work as advertised. Unfortunately, this is rarely the case. Browsers – and especially multimedia add-ons – have bugs in them. Pulling a random example out of a hat, here’s a Flash privilege escalation bug from earlier this year. The long and the short of it is that if I were to write an appropriately evil Flash app, I could do anything on your computer that the user running the browser could do.
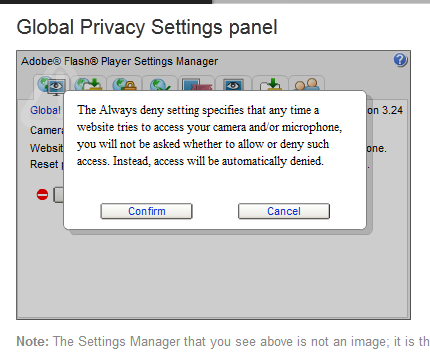
My favourite example is simply that of reading, writing and modifying files. I might get away with using Flash to plant a trojan or other form of malware, but so what? The public is completely inured to such risks and nobody is going to take that seriously. The far more shocking – but entirely possible – hack is simply to use this power to overwrite Flash’s own default settings file. From here, I can set Flash not to pop up a warning when it turns the webcam and microphone on.
Suddenly, Adobe Flash is literal spyware.
That very same trick could be used to change browser settings. This includes reenabling Java so that even more havoc can be wrought, disabling all your carefully assembled plugins and more.
It is for this reason that I strongly advocate either the complete removal of Java, Silverlight, Flash and the disabling of JavaScript, or the use of NoScript-level security on any and every browser. All it takes is one bad website to get Flash or Java open, and all your carefully crafted privacy defences are wiped out.
On the horizon
HTML5 is a huge threat to privacy, and both browser makers and web standards bodies are slow to respond. The European Network and Information Security Agency has identified 50 problems so far, and more are sure to follow with further research.
The online privacy arms race has only just begun. ®
How to stay anonymous - A Register Guide
Part 1 How websites use your browser to sell you for cash
Part 2 The Evercookie: Like trying to kill Steven Seagal
Part 3 Browser privacy at work: The BOFHs' guide