This article is more than 1 year old
Adventures in Tech: Taking the plunge into IPv6
Our intrepid reporter does it, but you'll still have to
THE WEAKEST LINK IS YOU
Recent commodity operating system versions such as Windows and *nix (including Linux and Mac OS X), and language libraries (eg C/C++/C#, Java, etc) support IPv6 one way or another, and network tools and browsers generally do too.
So the weakest points are likely to be:
- Old in-house servers/OSes and routers/bridges/switches.
- Your ISP and its routers to the Internet cloud.
- Your in-house code, server- and client-side.
The first may not matter if those parts of your infrastructure can ignore the IPv6 world and, for example, talk only to other internal machines.
Do make sure that your ISP or hosting company can support IPv6: I can't get it over ADSL to my home office (yet) but it's been available at one of my colos (Bogons) for a while, though I was not taking advantage of it.
You may still be able to tunnel out to IPv6-land even if your ISP or hosting company can't deliver it directly. For example, moderately-recent Mac OS X contains a "6 to 4" tunnel that can be turned on from the "Network" System Preferences with a couple of clicks provided that your machine has a public IPv4 address and a tolerant firewall: job done.
Try http://test-ipv6.com/ to test your IPv6 connectivity quickly from your desk.
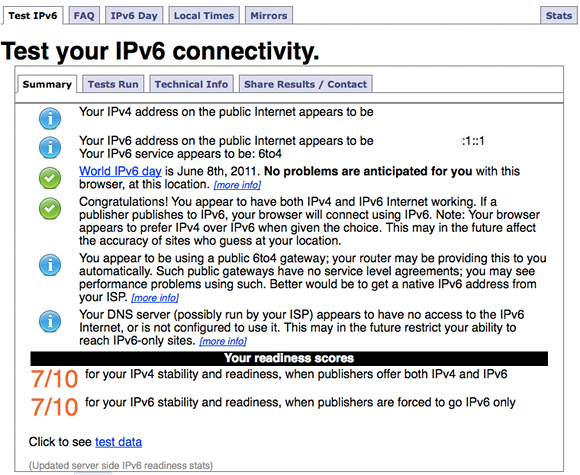
How http://test-ipv6.com/ looks in your browser when IPv6 tunnelling is working!
The real IPv6 Gordian Knot is likely in many cases to be that soup of half-brained it-kinda-works stuff known as in-house code. It may assume that an IP address is always 4 bytes (or can be entered or displayed as a dotted-quad) for example; think of space on reports, in database fields, log formatting, etc, etc.
So here is where you should start that Y2K-like testing: look for any references to, storage and logging of, and conversions to and from network names and addresses, especially IPv4, in the code: a decent IDE or static code analyser will help no end, but so can 'grep'.
And of course there is the magic of manual and automated testing: look at existing system unit and other tests, and write some more while you poke around.
For example, the (Java-based) site that I am adding IPv6 support to (it makes a slight effort not to be v6-foolish, but not much more) falls over spectacularly sometimes when I run up a local dev copy and connect to it locally as "localhost" rather than "127.0.0.1" because localhost sometimes gets expanded to the "::1" IPv6 loopback address and blows my code out of the water expecting a 4-byte address. So there's one area I could attempt to unit-test once I've drilled down to fix the root cause for example.
MY WAY ON THE SUPERHIGHWAY
So how was my experience in upgrading to support IPv6?
Well, it's not that I haven't thought about the coming upgrade fleetingly on and off for several years, so I didn't knowingly build anything stupidly incompatible. For example, for every OS install I did I made sure to enable IPv6 if that wasn't automatic, and all the variants of *nix, and the Java language that this site runs on, and my Tomcat servlet containers are all IPv6-friendly too.
But I kept running out of round tuits.
This time I stuck at it and spent maybe a day or two spread over 10 days to get to a working (not pretty, lots of rough edges to sand down) IPv6 server with its own DNS entries and ... ahem ... about 0.2% of my visitors!
The upgrade work was not that difficult in the end, especially as I wasn't in an externally-imposed panic. Do it before it does you!
In the next part I'll explain in more detail how I got on... ®
REFERENCES
Some light IPv6 reading to warm up!
- WTF is IPv6?
- IPv6 tunnelling (see image)
- Test your IPv6 connectivity quickly (JavaScript-based)
- The Netalyzr detailed connectivity check (Java-based)
- The "heise Online" dual-stack experience
- Wiki goodness on IPv6 addressing
- World IPv6 Day FAQ
- After World IPv6 Day "the consensus was that more work needed to be done before IPv6 could consistently be applied".
- For RFC3596: DNS Extensions to Support IP Version 6.
