This article is more than 1 year old
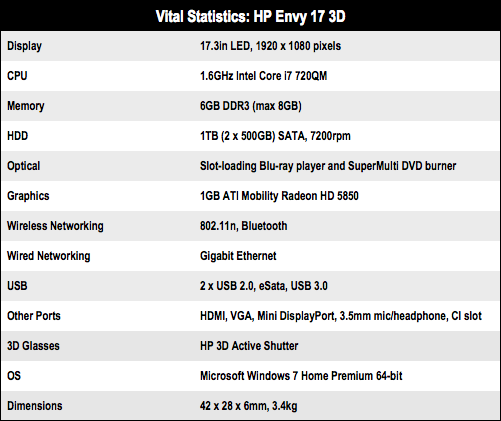
HP Envy 17 3D Core i7 laptop
Tasty 3D take away
The 17.3in LED display is sharp and bright at a wide range of angles, its 1920x1080-pixel resolution allowing it to support full 1080p HD media. To this end, the computer is fitted with a slot-loading Blu-ray player/DVD burner combo drive.

It's not really as thin as this picture makes it appear, but it’s more compact than most 3D luggables
Most connectivity ports are arranged on the left-hand edge of the case, plus two USB ports on the right-hand edge along with the optical drive a 5-in-one memory card slot. There’s a potentially useful combination of eSATA and USB 3.0 alongside the USB 2.0 ports, otherwise you can use all four for standard USB 2.0 devices. As well as HDMI and VGA connectors, the Envy 17 3D provides a Mini DisplayPort, although I did not get the opportunity to test whether it can be used as a Thunderbolt interface, but I’d guess not.
In use, the Envy 17 3D is a decent performer, automatically making use of Intel’s Turbo Boost technology to push the four cores of the Core i7 720QM processor to a maximum of 2.8GHz. This is not something a regular user can control: the Turbo Boost triggers apparently when it feels like it. But despite some good-but-not-staggering general benchmark results, the Envy 17 3D is a strong gaming computer.
Its 3D display feature is nicely implemented, enabling itself automatically when appropriate but not stupidly splitting or blurring the screen when it isn’t. HP’s 3D shutter glasses also switch themselves on automatically when they detect the 3D sync signal from the computer, so there’s no fiddling around playing hunt-the-microscopic-button whenever you feel the sudden impulse to sit down and play.
Benchmark Tests
PCMark Vantage Overall Results
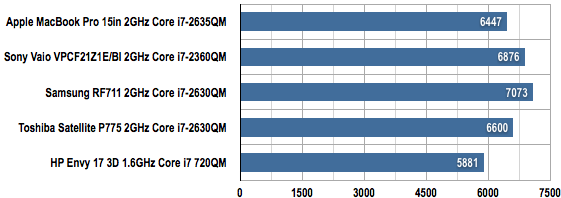
Longer bars are better
Battery Life Results
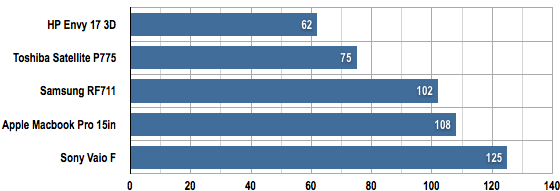
Battery life in minutes
Longer bars are better