This article is more than 1 year old
Key internet address server sees spike in traffic
K-root down, but not (yet) out
Traffic hitting a key internet address look-up server in Europe has spiked over the past 24 hours, reaching loads that are four times higher than normal.
It's still not clear what's causing the sharp increase in queries to the K-root, which is maintained by the RIPE Coordination Network Centre. Engineers with the Netherlands-based regional internet registry said they are analyzing the traffic and communicating with internet service providers to learn more about the source of the queries.
The RIPE advisory said the increased load also hit other root servers, which are the authoritative source for translating domain names into their computer-readable IP addresses. In all there are 13 servers, or clusters of servers, maintained by various organizations around the world. The spike hasn't had a dramatic effect on response times in the root zone.
"You will notice that only a few test clients were affected because not all anycast instances of K-root were subject to the increase in traffic," the RIPE engineers wrote. "Also not[e] that we successfully mitigated the effect of the increased load even further around 6:30 UTC."
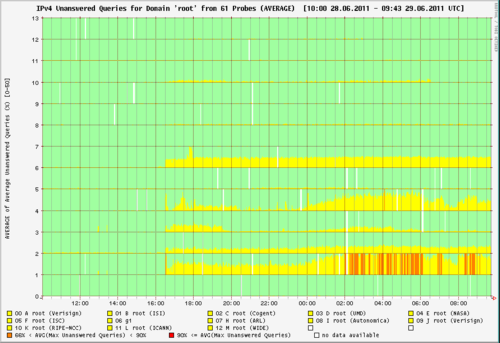
Unanswered queries for each root. Chart supplied by RIPE.
The engineers have shifted traffic from Amsterdam to London to gather data about its source. Figures supplied by RIPE showed that the B, C, E, and G roots -- operated by the the University of Southern California, Cogent Communications, NASA, and the Defense Information Systems Agency, respectively -- were dropping more queries than the K root was, although the cause wasn't explained.
"Not certain what is behind it other than an unusual amount of address queries for .com domains," Randal Vaughn, a professor of information systems at Baylor University, wrote in an email to The Register. "If I am reading the rolling graph on http://dns.icann.org/ [correctly] it seems the traffic may be decreasing." ®
