This article is more than 1 year old
EMC and NetApp on a roll
Storage pure plays kicking ass
Pure play storage suppliers EMC and NetApp are outpacing the server and storage system players Dell, HP and IBM, with Compellent, 3PAR, Storwize and XIV the main catch-up bets for the three followers.
Dell bought Compellent to expand its enterprise storage business in roughly the same way that HP bought 3PAR. We can fit IBM's purchase of XIV and Storwize into the same mould.
Stifel Nicolaus analyst Aaron Rakers has been tracking these five storage suppliers and says he sees a bifurcation happening. EMC and Netapp, the two pure play storage companies (meaning they don't sell servers, essentially), are outpacing Dell, HP and IBM by gaining market share based on revenue. He has produced a chart that shows this:
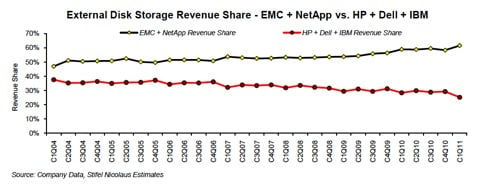
Storage supplier market share bifurcation (Stifel Nicolaus)
The bifurcation started becoming apparent in 2007 and has continued since then, with the gap steadily widening. In the latest quarter on his chart the gap has widened again, indicating that the three following suppliers - Dell, HP and IBM - have their work cut out if they are to regain their lost market share.
A second chart has NetApp growing its storage market share far higher than any other supplier, including EMC:-
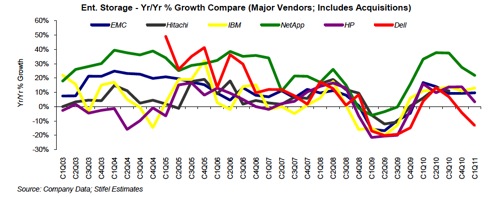
Storage supplier growth rates (Stifel Nicolaus)
NetApp has had a growth rate advantage since 2009. It has a long way to go to catch up with EMC in storage revenue market share terms though, as EMC has around 45 per cent compared to NetApp's 18 per cent. On this chart EMC, Hitachi Data Systems, and IBM are all doing better than HP and Dell.
If both IBM's Storwize and XIV strategies, and EMC's VNX strategy pays off, either or both could equal and perhaps overtake NetApp. Hitachi Data Systems is also in this category as NetApp's year-on-year growth rate is continuing down, paralleling HP and Dell. ®
