This article is more than 1 year old
Intel's future Sandy Bridge Xeons exposed
x64 iron choices galore
A 'Patsburg' for every need
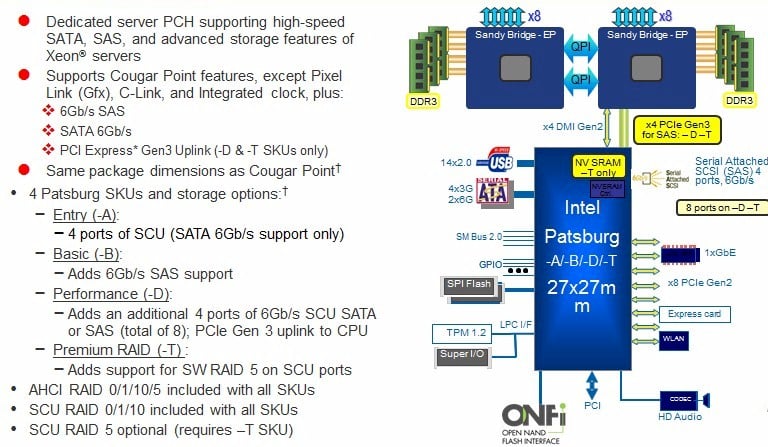
A lot of the variation that Intel is baking into the Romley platform is coming from the Patsburg chipset, which is coming in four different flavors, the C600-A, C600-B, C600-D, and C600-T. Here's how the different peripheral features of the Patsburg variants stack up:
By making a variable Patsburg chipset, Intel can deliver different functionality at different price points and do a better job of competing against AMD, which is trying to win hearts and data center budgets straight out on low pricing with two different processors in two sockets and three chipset variations. If Intel can best meet the needs of different server customers by having a range of I/O options – allowing server makers to only put the features customers absolutely need and will pay for into each box – then Chipzilla has a good chance of deflecting what we assume will be a very aggressive Opteron 6200 in the summer and then Opteron 4200 launch later in 2011 or perhaps early in 2012.
In any event, the Patsburg-A chipset supports four 6Gb/sec SATA ports for disk drive or solid state drive storage. The Patsburg-B chipset adds support for 6Gb/sec SAS peripherals. Both of these Patsburg variants seem to use the x4 DMI Generation 2 interface that Intel created for linking on-chip HD Graphics coprocessors to the CPUs. The Patsburg-D chipset adds four more SAS or SATA ports and a PCI-Express 3.0 uplink to the CPU to carry the extra load. All three of these Patsburg chipsets offer software-based RAID 0, 1, 5, and 10 data protection on the SATA ports and RAID 0, 1, and 10 protection on the SAS ports.
If you want RAID 5 protection on your SAS drives, you need to buy a machine with the fourth Patsburg-T variant. The T variant of the C600 chipset will also support non-volatile storage (NV-SRAM), and it seems reasonable that this will be a cache for the RAID 5 disk arrays implemented by the chipsets. ®