This article is more than 1 year old
Creative Sound Blaster Tactic 3D Sigma gaming headset
Spatial delivery
Crystal set
Configured this way taps into the headset’s THX TruStudio Pro software. Easy to use and instal, it’s better looking than the actual headphones with pleasingly large volume and mic controls along with a pretty 3D modelled forest scene to test video. Being a customisable skin, naturally I set the appearance to a purply pink.
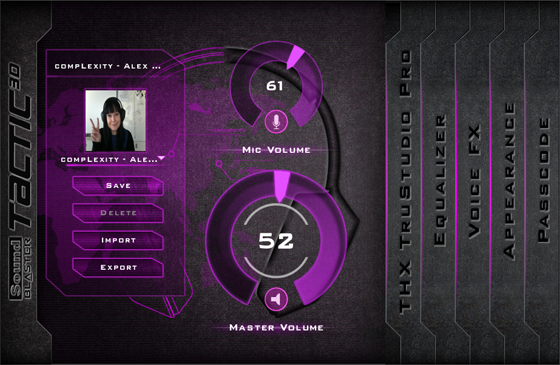
Besides interface customisation, the large controls can also be altered from touchscreen PCs
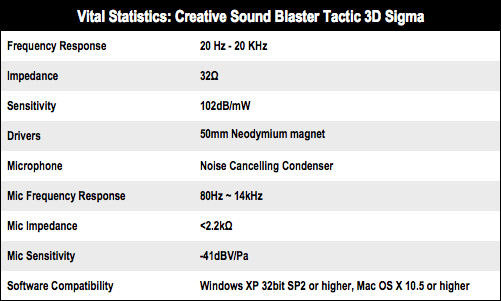
The Sigmas have impressive frequency response from 20Hz to 20kHz and testing with the Beastie Boys album, Hot Sauce Committee, really showed off the intense, penetrating output this headset can deliver. From the off using the default settings, the Creative Sigmas can definitely do loud, without distorting.
Among the settings is the Crystalliser, which is supposed to add “pop” or sharpness to compressed audio, but despite fiddling with it, I found it didn’t seem to do anything impressive. Lest we forget LiveTouch, the interface's touchscreen compatibility, which is all well and good but I don’t know anyone who owns one. For fear of this review appealing to anyone under the age of 18, I am not even going to mention the voice morphing, but let’s just say I left it on emo.

TacticControl THX Sound Control Pro sound enhancement settings
The main selling point of these headphones is the 3D audio – delivering 5.1 and 7.1 soundfields from just two drivers with Creative's THX TruStudio Pro audio technology. After altering the Surround control when playing Left 4 Dead 2 I did find it quite immersive. I could hear the witch crying and the horde running clearly from the front, back, above and below. Woah, watch out for that helicopter!