This article is more than 1 year old
Samsung Galaxy S II dual core Android smartphone
Speed dialler
Review Sometimes the Mark II versions of phones feel like they’ve had little more than a light skim with the update brush. Yet with the Samsung Galaxy S II, this is certainly not the case. While, the original Galaxy S was a fine handset, this latest refit includes dual core processor, stunning AMOLED screen, a fine 8Mp camera, over-air syncing and more, all packed within one of the slimmest enclosures you’re likely to come across.
Second coming: Samsung Galaxy S II
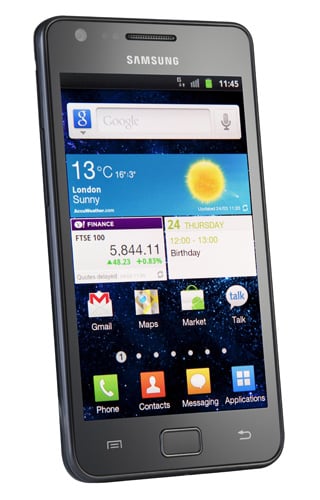
The handset measures 125 x 66 x 8.5mm, which almost makes it feel more like a stretched out playing card than a top-of-the-range Android smartphone. Not only is it very slim, at 115g it’s very light too, though part of that can be attributed to the rather flimsy plastic back panel.
The front mostly consists of a single sheet of glass, surrounded by a thin metal rim, with a single hard home button at the bottom. Pressing it kicks the screen into life and reveals a touch sensitive button on either side: back and menu, but no Android search button.
On the sides are a slimline volume rocker and power button, with a 3.5mm headphone jack on top and a micro USB power/sync slot on the bottom. Indeed, everything is where it should be, although there’s no hard camera shutter button.
Technically speaking, the 4.3in screen’s 480 x 800-pixel resolution may not be quite as sharp as the iPhone’s 640 x 960, but in use, you’d hardly notice. It looks great, with extremely vibrant colours and very bright too, which helps when you’re looking at it in sunlight, along with its very wide viewing angle too. The screen’s not just a pretty face either, since it’s admirably sensitive, distinguishing between brushes and presses with ease.

Slim, for sure
The Galaxy S II is one of the growing band of dual core handsets, intended to deliver ultra-fast processing leading to more complex gaming, super smooth hi-res film viewing and advanced multi-tasking, despite the potential to exact a heavy toll on the battery life.
