This article is more than 1 year old
The Sandy Bridge Hackintosh
Run Mac OS X on Intel's new Core i
Juggling Disks
At this stage, we're still running off the Apple installation DVD, and we need to install everything onto a drive. The installation will be looking around for a suitable disk, and won't find one: you'll need to format the drive before the installation will condescend to settle on it. For this purpose the Mac Utilities menu offers Disk Utility.
Select the target drive in the left-hand column, and pick Partition from the function tabs on the right. Set the Volume Scheme to "Single Partition" and make sure the Format type is "Mac OS Extended (Journaled)". Click the Options button, and make sure "GUID Partition Table" is selected.
Once partitioned, the drive appears as installable, and you can now take a 40-minute break while everything gets transferred across. When you get back, the chances are you'll be greeted by the following message:
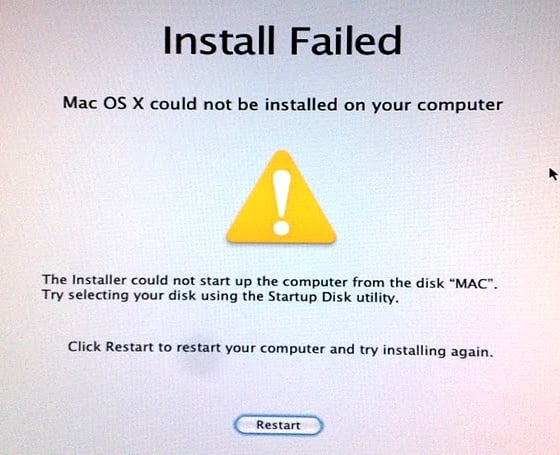
Hmmm. To Thomas Edison failure meant "I've succeeded in discovering yet another way in which this won't work". What you've discovered here is that you still need the iBoot disc. Boot off this again, select the drive on Sata 0... and now discover that the installation has in fact succeeded beautifully.
Beyond the Desktop
Keen Hackintoshers are suffusing netbooks and notebooks with Snow Leopard goodness too, but here the hardware limitations tend to be more stringent. A machine with an Intel Atom processor, 1 GB of RAM, an absolute minimum of 8 GB hard drive space, and the GMA 945/950 graphics chipset is a very likely candidate. If your machine fits this description you can turn straight to mechdrew's guides and use the method based on Mechlort's NetbookInstaller Suite.
My own MSI Wind isn't on the hardware compatibility list (HCL) for NetbookInstaller, but I thought I'd take a punt with it anyway. The NetbookInstaller Suite has two components: NetbookBootmaker, which creates a bootable USB stick for the installation, and NetbookInstaller, which tweaks the installation for your particular hardware. The USB stick created by NetbookBootmaker and the NetbookInstaller app are roughly comparable to tonymacx86's iBoot and EasyBeast.
Following the methods outlined here, I achieved a workable Snow Leopard on the Wind. A key feature missing was the wireless connection, and the recommended fix for this is to replace the wireless hardware - it's normally just a plug-in component - at a cost of between ten and fifteen quid.
