Home made
This process is, essentially, the reverse of a traditional milling machine, which cuts away material from a solid block to create an object. One of the advantages of additive manufacturing is that there’s much less waste.

HP's 3D printing rig costs around 11 grand
One of the commonly used materials for this sort of work is a polymer, like ABS, extruded from print heads that look a little like a glue gun. You’ll find countless examples of objects like clothes hooks, cups, and fairly simply objects. But that’s by no means all that can be created, or the only way of doing it.
For objects like those titanium aircraft parts, powdered metal particles are fused together with a laser, a process known as sintering. In stereolithography, a laser focuses on the surface of a vat of polymer, causing localised hardening – you can see the process in action in this video – and very complex designs can be created.
Clever software will even automatically add supporting structures, so that you can create designs with internal spaces or overhanging sections, either simply snapping them off or – in the case of systems like the Object Polyjet - by flushing them out with water or dissolving them.
That, in fact, is one of the key things to remember about the current generation of 3D printing systems: many of them don’t produce a fully finished product, and require extra steps like removing supports, or curing polymers using ultraviolet light, before the object is finally ready.
3D printing isn’t the sole preserve of the professional manufacturer. There are several projects that aim to make it easy for just about anyone to print objects at home. One of the most well know is RepRap - read more about this one on my blog. It’s not the only one: there are several similar projects, such as Makerbot and Fab@Home.
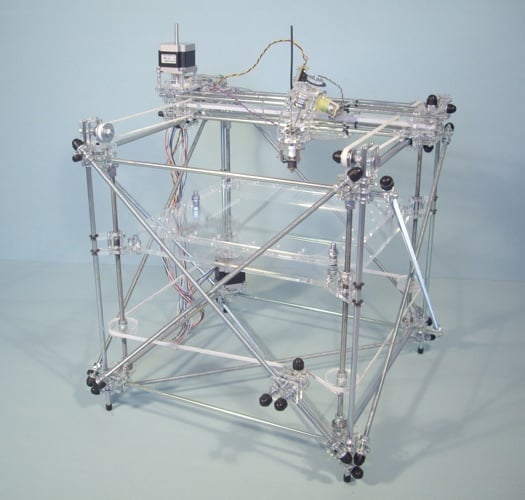
The RepRap rig, built by Bits From Bytes
Typically open source, you can put together a printer based on one of these systems for under a few hundred pounds, or buy one ready built for under £1000. There are libraries of basic designs that you can download and create, or use as starting points for your own objects, from sites like Thingiverse.
