This article is more than 1 year old
Make vision elementary
Sleuths and other BI data visualisation data apps
Workshop “Vision is the art of seeing what is invisible to others.” Jonathan Swift’s observation applies perfectly to crime detection.
Thanks to data visualisation, the toil of thumbing through card index boxes to trace the links between people and find connections in large amounts of data is fast being replaced by visual maps of suspects and known criminal activity. Such software, known as Social Network Analysis (SNA), can already be applied to sites like Facebook to trace the associates of a given target.
One company that produces tools used by police forces, defence and intelligence agencies and commercial organisations to uncover hidden connections is US-based i2.
According to Julian Midwinter, vice-president of i2, visualisation enables data from spreadsheets, surveillance videos, phone records, IP addresses and more to be analysed much faster. “Not long ago an analyst took more than 25 hours to extract information from one chart. With SNA it takes only a few minutes,” he says.
At the same time, by linking to real-time data and sharing the output over intranets, security services can cooperate and react much quicker than before.
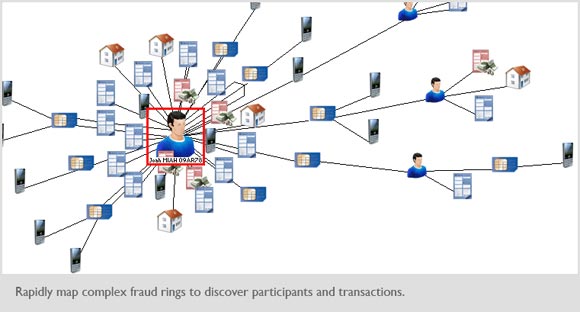
“The holy grail is to find a piece of critical information that prevents a catastrophic event – a terrorist incident, a crime in the commercial world, or a discovery of fraud that saves a company from financial disaster,” says Midwinter.
On a slightly more mundane level, data visualisation is increasingly being used by businesses to improve access and analysis of key data as part of a business intelligence (BI) strategy.
Gartner’s Magic Quadrant for Business Intelligence Platforms recently ranked Microsoft, IBM, SAP, MicroStrategy, Information Builders and SAS as “leader with high ability to execute”. Microsoft's unusual focus, according to Gartner, is on "information worker" productivity to make its tools attractive for organisations that want to make BI capabilities more pervasive. One reservation, however, was that there is no single metadata layer across Microsoft’s BI platform components.
Gareth Arnold, Visio product specialist at Microsoft, says BI is key to recent improvements in Visio 2010. “Diagramming software gets really interesting when you start to use it to extract data. It means you can set up all kinds of scenarios for cost control and company analysis,” he says.
In a different sphere, Microsoft is using Visio linked to Exchange to give instant views of the company’s human resources (HR) chart. Authorised staff can select parts of the chart and HR updates on Exchange automatically feed through to any user of the chart. It can also give line managers budget and spend details, and diagrams connected to real-time interactive data can be shared with others across the internet.
But not all the benefits of BI come straight out of the box.
Al Edlund, a US-based expert on visualisation, says: “The strength of Visio lies in its ability to provide many different disciplines to get into the diagramming of business issues. The weakness is that many of the add-ons are at an introductory level and since the MS code is not open source, they are not extendable. There is a pretty steep learning curve on some of this because if you want to step into the MS vision of datalinking you have to come in with skills in several different object models – .Net, database, office products, and so on.”
Arnold disagrees. “The advanced diagramming tools in Visio are easy to use. Anyone can easily place real-time data right into the shapes of a diagram,” he says.
Although some complex BI applications need coding expertise, it is clear that leading diagramming tools are increasingly becoming a central repository for data, displaying multiple sources at one time, allowing users to control the refresh rate of any feed and offering the ability to extract data from the diagram.
According to the Gartner report, it’s about visuals superseding reports. The authors write: “Organisations are rapidly embracing the idea of providing data to end-users and empowering them with an ability to navigate and visualise the data in a ‘surf and save’ mode, as an alternative to a ‘report-only’ functionality.” ®
