Media savvy
Although it works well, the only real advantage of using the iXtreamer over an Apple dock is the ability to browse your music library on your television. If you wish to view pictures, you must manually start the slideshow on your iOS device first. This kind of behaviour makes the experience feel unfinished, almost as if there was no real effort to implement proper support.

Hook it up to an USB DVD drive and it'll play discs too
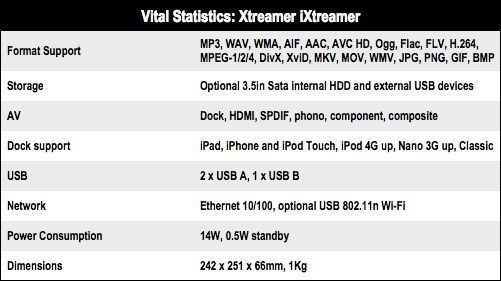
Docked Apple devices aside, the iXtreamer is actually quite a capable media streaming box. Despite lacking a gigabit Ethernet connection, featuring only a 10/100Mbps LAN port, even 1080p video can be streamed if encoded using modest compression. Users may encounter issues with higher bit-rate files, but this is really to be expected without a gigabit connection.
Also pleasingly, the iXtreamer supports a large number of media types, unlike other proprietary solutions that can be quite restrictive. Although the iXtreamer features support for most UPnP media servers such as TwonkyMedia and TVersity, it lacks support for the iTunes DAAP protocol, something which should surely be present as this is a product clearly targeted towards Apple users.
Aside from the usual local streaming features, the iXtreamer packs a fair number of open-source community developed goodies under the Xtreamering menu. These include a Grooveshark jukebox (requires a paid Grooveshark Anywhere account), xVOD – a MegaVideo streaming service, Xtreamer Live, YouTube, Internet TV through Xtreamer On Air, along with Internet news and weather services.
It doesn’t stop there though, there’s yet another feature. Through the use of a USB or networked DVD player, the iXtreamer can also play your DVD collection. Using a Plextor PX-L611U external USB DVD writer, I found playback to be of excellent quality, in fact just as good as any standalone player I have ever used.