This article is more than 1 year old
SaaS security: it comes down to knowing what you are doing
Roundup of discussion from Week 2
In this workshop on Software as a Service (SaaS), we’ve been having a good look at the issues of risk, trust and security in the cloud. A lot of things have happened recently that may cause us to think twice about SaaS and risk – Flickr showed just how absurd things can get if policies and processes are not properly thought through and managed. It also brings into sharp focus once again the importance of supplier selection and contract terms.
Reg readers have been pretty forthright about their nervousness regarding security and privacy with hosted apps, and it's all too easy to focus on the negative stories as they make good headlines and stick in the mind.
Stepping back from the headlines, we’ve run a structured survey to put the discussion of SaaS security and privacy on a solid footing and gain some perspective on what is for many a highly emotive topic. The results that came back revealed some sharp divisions in opinion and also exposed some uncomfortable truths.
SaaS security is often considered in isolation, while we tend to forget the bigger picture – on-premise security has its limitations and remains challenging. One of the most prominent results that came through in the survey, and one that is consistent with our previous research, is that on-premise security is a continuing issue for many companies. What is in place may be felt to be 'good enough' by many, but the reality is that internal security is still far from where respondents ideally want it to be. The road to security nirvana is paved with competing pressures for time, manpower and budget.
Meanwhile, for all the worries you expressed about SaaS security, the risk of data leakage is perceived to be high within many businesses. This is felt particularly acutely as personal devices and services are increasingly used for work by a workforce that pays scant attention to IT security.
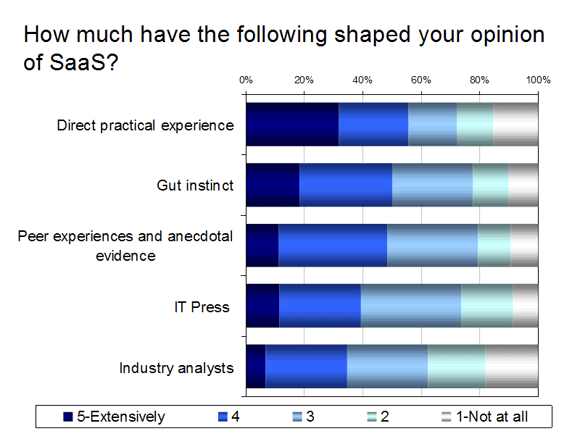
Stepping back and looking now at attitudes to SaaS security, it is clear that many have deep rooted concerns despite their own in-house worries. In order to understand why this is, it is useful to look at what is most influential in shaping their views. Most of the respondents have very little experience of SaaS, if at all. It is also telling that these inexperienced respondents mainly use their gut instinct to shape their opinion of SaaS.
In addition, the consensus of opinion from respondents is that security and privacy are significantly worse for SaaS than for on-premise solutions and for many, this is sufficient to put SaaS options on the backburner. It's also abundantly clear that SaaS providers tend to be lumped together, regardless of their sophistication and capabilities of their services.
The big question that we need to answer here is whether these fears are founded in reality, or more to do with an abundance of natural caution towards things that are new, unknown or unfamiliar. In order to glean the answer to this, we need to look at how the opinions on SaaS security and privacy differ between the majority with little to no experience of SaaS, and the minority of respondents who use it extensively across multiple areas of their business. What emerges is a radically different perception of SaaS security between the two groups, and one that should give CIOs and CSOs pause for thought:
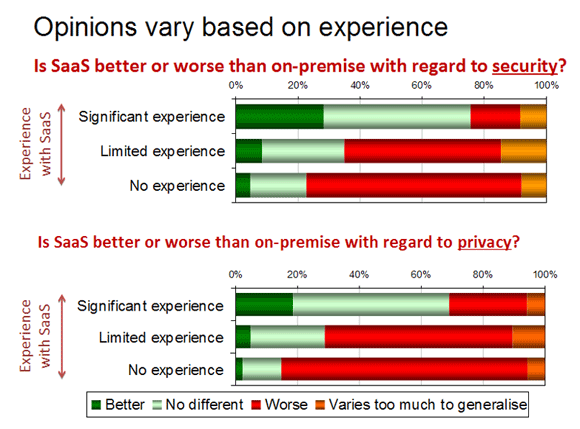
This shift in attitude is significant, because it moves the issue of SaaS security and privacy from being a blocker, to instead being neutral for most and even an enabler of adoption for some.
Of course, this does not mean that every service is equal. Some providers may indeed be shocking in their security, not to mention their other capabilities. It does mean that where a provider has been subject to a comprehensive review and analysis and can meet the business requirements, SaaS should be able to compete on a level playing field with on-premise solutions in terms of security and privacy.
So, what should we be taking away with us from this workshop on hosted applications? If anything, it's that there is a lot of fear, uncertainty and doubt surrounding SaaS and security, and it is felt in a very real manner.
These fears take time and experience to assuage, but there are many who clearly have overcome the fears and are deploying SaaS extensively and a good proportion feel very positive about doing so. The end result is that once the SaaS security issue can be put to bed, the selection process can focus on the business requirements that need to be solved and the overall fit of the service to meet these needs compared to the other options on the table. ®
