This article is more than 1 year old
Mobile data streaming overtakes downloading
But it's apps that fill the airwaves
More data is now being streamed to mobile phones than downloaded.
The figures come from Allot Communications, as part of its biannual Mobility Report, and drawn from analysis of the traffic delivered to 210 million mobile subscribers around the world. That analysis shows video streaming continues its steady growth as the killer use of mobile data, but that Apple's domination of app deliveries remains complete, for the moment.
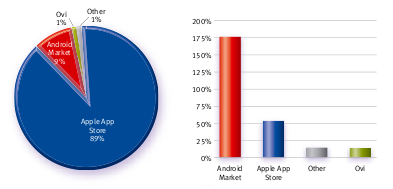
The growth rates, on the right, show how things might develop for next time
The figures for application stores are new in this report, so there's no historical data to compare with. The data also shows the volume of data consumed by downloading, not the number of applications downloaded - so it could be that Ovi apps are just really efficient and thus tiny, but it isn't. Worse than that, Allot's figures only include over-the-air downloads, so all those side-loaded apps bought through desktop iTunes aren't counted at all.
But we already know that Apple sells a lot of apps; more interesting is the way that media streaming and file downloading have switched places over the last 18 months.
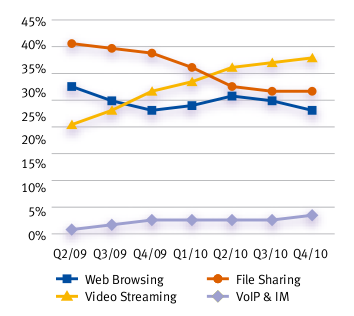
Video streaming and file downloads almost switch places
That might be down to the proliferation of commercial streaming services, but it can also be attributed to the more intelligent use of smart phones as they replace dongle-equipped laptops as the dominant consumer of mobile data. It may be possible to run BitTorrent on a mobile phone, but not a lot of people are doing that and YouTube is for everyone.
Allot don't distinguish between streams delivered within a browser and those consumed by mobile applications, but one way or another mobile users are tapping into Facebook and Twitter in huge quantities. Twitter jumped almost four times in the second half of 2010, while Facebook traffic more than doubled over the same period.
During 2010 mobile data traffic increased by 190 per cent, showing there's still a huge appetite for data on the move. How much of that is increased consumption by individuals - as opposed to new users coming online - Allot doesn't record, but it's an interesting question to consider. ®
