This article is more than 1 year old
Samsung Galaxy Player 50 Android PMP
Smartphone sans phone?
Android, pimp my PMP
On the positive side, you connect the Galaxy Player to a computer using a Micro USB rather than some strange Korean cable, and both USB port and the 3.5mm audio jack are well placed, on the top of the device.

Simple, effective sound tweaking tech
The usual Android Henu, Home and Back buttons sit below the screen, the middle one a physical button, the other two touch-sensitive. Volume aside, everything is managed using the capacitive multi-touch screen, which is both fluid and responsive.
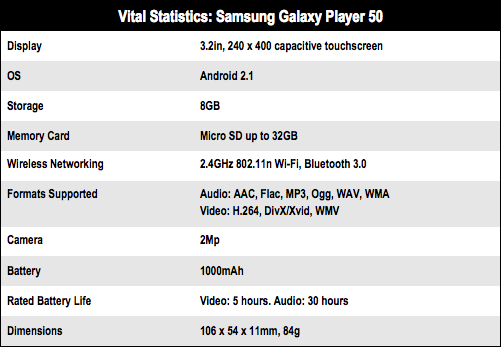
The Galaxy Player has 8GB of built-in storage with 1GB of that available for downloaded applications. Or rather it was before my Galaxy crashed after switching the USB Debugging feature on. At that point, the 1GB vanished, never to reappear. Under the battery cover is a Micro SD card slot good for another 32GB of - please note - unified storage.
As I said, what I have here is a pre-production model so hopefully that accounts for this problem - and for the device forgetting my Wi-Fi security code, and changing the wallpaper and desktop arrangement back to the default every time I turned it off.