This article is more than 1 year old
10 top New Year's Eve party apps for iPhone, iPad, iPod touch
Eats, drinks, tunes, games
Tunes
The idea behind Party Playlist HD (iPad, $1.99 or a free "lite") is a simple one: to make it easy for you or your guests to create party-specific playlists on the fly.
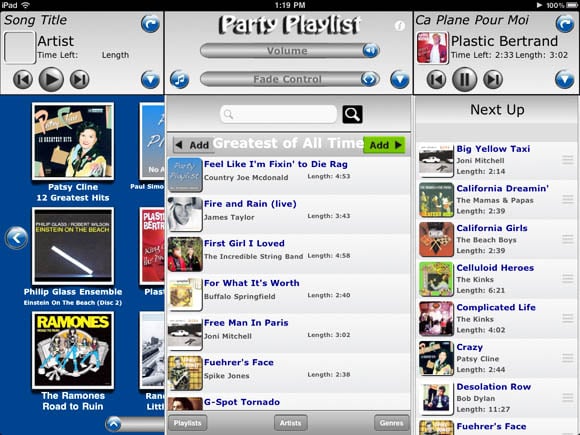
Let your guests reorder party playlists. Well, guests with reasonable taste, that is...
Party Playlist scans your iPad for the tunes you've loaded onto it, arranges them into your playlists, displays them by album cover, then lets you drag them into new playlists and rearrange their playing order while they're being pumped out through the iPad's headphone jack into your sound system of choice.
If your iPad doesn't contain enough party-worthy tunes, Minimal Party HD by mix.dj (iPad, free but ad-supported) accesses mixes from the Mix.dj website, which contains over 100,000 DJ-created compilations averaging around an hour long apiece.
Minimal Party's minimalistic, electronica-flavored mixes may or may not be your cup of tea, but at this price the app is well worth a look-see. And if you like one or more of the tunes in a mix, the artists who uploaded their mixes to Mix.dj would be quite happy if you bought those tunes through an iTunes link in the app.
If you'd prefer to entice your party guests into making fools of themselves providing real-time entertainment, the App Store has plenty of karaoke apps to choose from.
Karaoke Anywhere (iPhone, iPod touch, iPad, $1.99) is unique among the karaoke apps that we found in that it can play the CD+G files used in professional karaoke machines. It may be more than the average user needs, but a true karaoke addict should take a look at its features on the KaraokeAnywhere website.
More casual karaokists might want to check out Glee Karaoke (iPhone, iPod touch, iPad, 99¢) from Smule, the publishers of a collection of "social music" apps, from Leaf Trombone World Stage to Magic Fiddle and more.
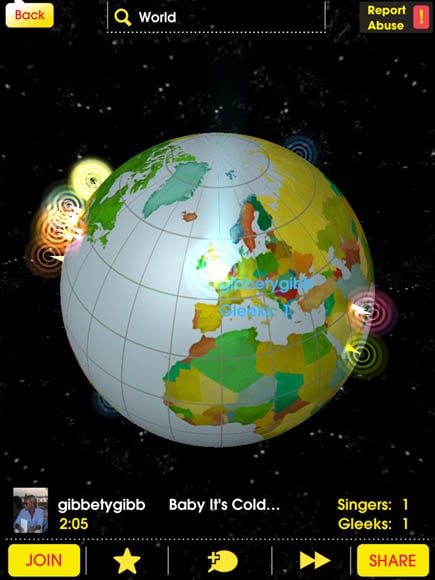
Glee Karaoke lets you listen in to brave amateurs from all over the globe
In addition to straightforward karaoking, Glee Karaoke – like other Smule apps – lets you share your talents with the world in real time, or lets you listen to other contributors embarassing themselves in London, New York, Sydney, Tierra del Fuego, and beyond.
