This article is more than 1 year old
Filthy PCs: The X-rated circus of horrors
Grotesque dust creatures and mummified frogs
Ventblockers II Well, you lovely people, it's time to pour yourselves a stiff brandy before entering the circus of horrors that is Ventblockers II.
Good work by all those readers who sent in evidence demonstrating that it really is a good idea to keep your computer spick and span. The consequences of poor PC hygiene can, as we shall see, be quite terrifying.
Of course, we're going to break you in gently, so let's warm up with a few dusty moments. Picoshark admits he "didn't have the nerve" to open this box in the warehouse where he works, so he just wrote a message for his boss, suggesting they should probably get some new kit:

Cornz, though, did have the cojones to open this machine from a builder's yard. He says it was "caked in really fine brick dust", and accordingly suffering somewhat from overheating:
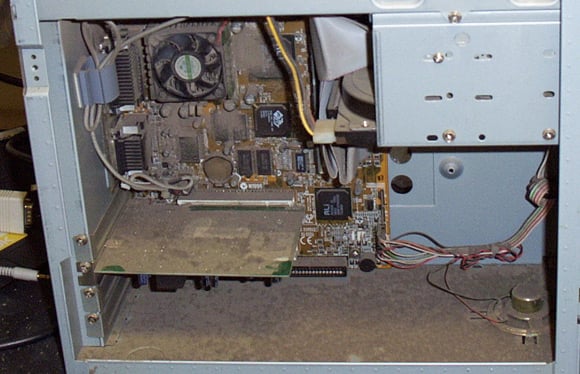
Roger Greenwood reports that he was "called to our welding and grinding shop" to investigate a clapped-out machine. Magnetic metal dust and computers don't mix, although five minutes with a compressed air gun were enough to get this PC up and running:

