This article is more than 1 year old
Rethinking the iPhone
The Swiss Army knife of telephony
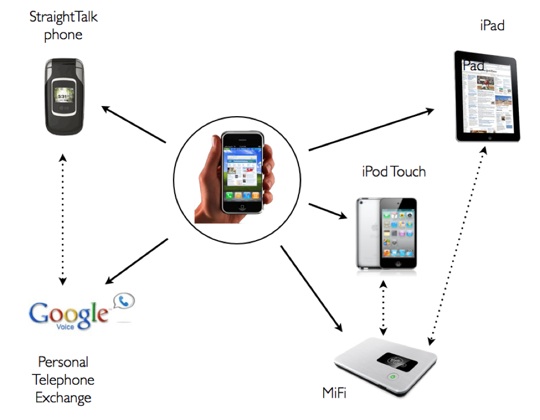
When I asked my friend Quentin recently how he liked his new iPhone, he said it was great, except as a telephone. He was right, and as a devoted iPhoner since its introduction, this made me think.
My carrier’s coverage (AT&T) is lousy, the 3G connection is slow/patchy and AT&T is expensive, on average $82 a month. I love the iPhone’s design, its Apps and look, and of course the “always-on” access to emails and internet it provides, but I recognized myself an over-user - constantly looking things up, checking/replying to emails in real time, and generally being a nerd!
So I decided to rethink the experience, especially as, on analysis, my 300 minutes average monthly phone usage was costing me a whooping 27¢ per minute - OK so this included manic email internet usage. This meant spending $2,168 over my two-year contract, if I include the $200 upgrade fee.
Recently, AT&T obligingly told me I had to wait several months before I could get a $200 upgrade to iPhone 4, which would trigger yet another two-year contract cycle. How I hate being in the hands of a telephone company!
So this is what I did: it retains all of the iPhone functionality, markedly improved my phone and internet experience, saved money and ended the two-year contract habit. And I can live with the minor compromise, which make me less manic.