This article is more than 1 year old
The forgotten, fat generation of Mac Portables
Long before the Air, there was Lord Lard Ass
A plethora of ports
Before we open up our Macintosh Portable to see what makes the beefy fellow tick, let's take a quick look at how it connected to the outside world.
The Portable came with a full complement of ports, comparable to those found in all-in-one Macs of its era, but with the notable addition of a DB-15 port for attaching an external display — an unusual luxury at the time.
The ports are gathered into two groups on the back of the box. On the right hand side are power and stereo audio-out jacks, one four-pin mini-DIN ADB (Apple desktop bus) port for adding a mouse, and two eight-pin mini-DIN RS-232/RS-422 serial ports that have AppleTalk/LocalTalk slo-mo networking capability, but are labeled with printer and modem icons.

As with all Macs since the very first, networking was built in — slow, but built-in (click to enlarge)
Separating the two groups of ports is an opening that would house the RJ-13 port of an internal 2400bps V.22bis modem card, should you have chosen to pop for that option. As you'll see when we open this beast up, the slot for the modem is easy to access — and to identify, being labeled, well, Modem.
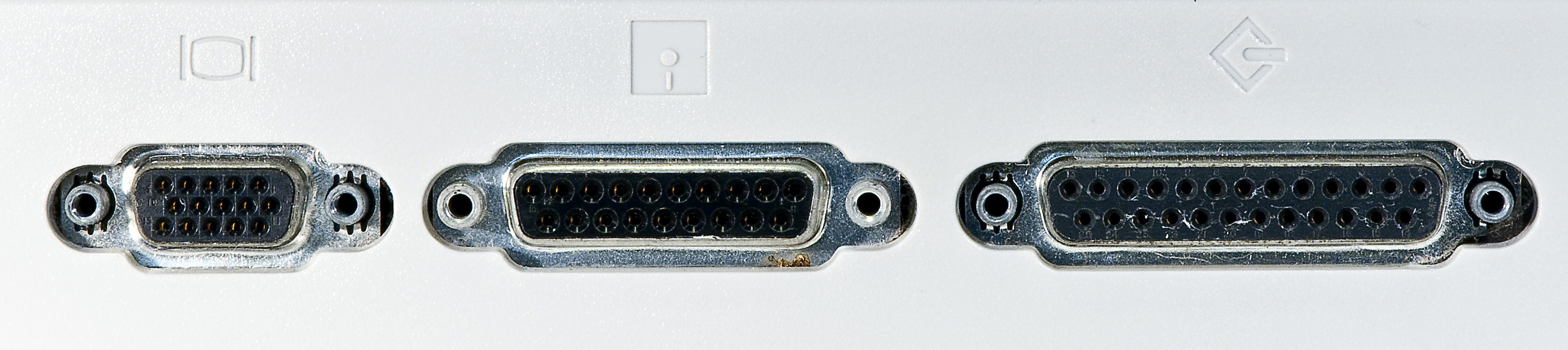
Over on the left-hand cheek of the Portable's rump is the aforementioned DB-15 external-video port, plus a DB-19 floppy port and DB-25 SCSI (small computer system interface) port that topped out at a whopping 1.5MB per second — theoretically, at least.
For you young 'uns, it may be instructive to learn that moody, unpredictable, termination-touchy SCSI didn't disappear from Macs until the original Bondi Blue iMac shipped in August of 1998. It was thankfully supplanted by FireWire 400, first in January 1999's blue-and-white Power Mac G3 — aka "Yosemite" — and then in the third iteration of the iMac in October of that year.