This article is more than 1 year old
Top Ten Retro PC Games
A blast from the past
Sim City 2000

A lot like the original SimCity, SimCity 2000 is focused on managing your land properties and resources. Yes indeed, it’s all about infrastructure. Keep your city growing and population happy, and you are in for hours of addictive game play. SimCity 2000 changed to an isometric aspect instead of the old overhead view, which allowed more depth with underground hidden layers. For its time the graphics on this game were really elaborate. I love this game because it is completely immersive and you’ve always got a natural disaster to cope with. F**K YOU Godzilla, that just took me a week to build!
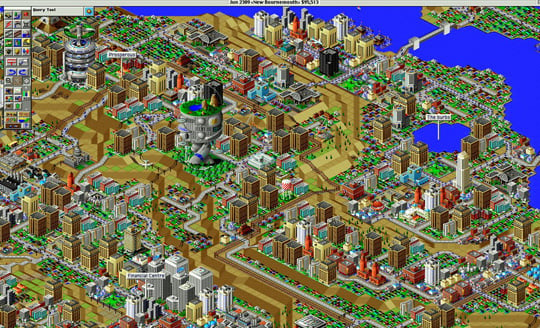
Developer Maxis
Year of release 1993
Command and Conquer

Command and Conquer took real-time strategy to another level and a wider demographic. The Global Defense Initiative and the Brotherhood of Nod are locked in a battle over a mysterious resource Tiberium, and it’s going to take all your tactical skills to conquer your opponent’s base. Its on-line multiplayer capability upped the mass slaughter and turned the genre from impenetrable, to captivating. Epic sound effects and music complimented with live action clips make this Command and Conquer stand out in its genre. Its impact can be measured by the long running franchise.
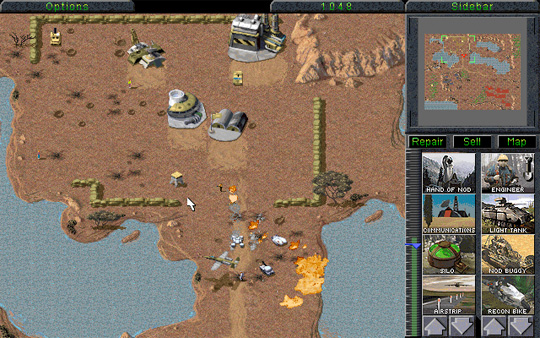
Developer Westwood Studios
Year of release 1995
