This article is more than 1 year old
iDapt i4 multi-purpose charger
Does 'em all, apparently
Review Charging cables inevitably get knotted, misplaced or mistaken, yet appear a necessary evil to keep mobile devices going. So many proprietary connections are in circulation nowadays and, with most people owning at least two devices, cables soon become a mess and families fight over plug sockets.

On multiple charges: iDapt's i4
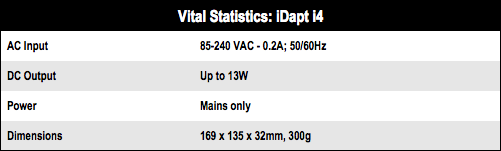
The iDapt i4 charging dock offers some respite from this situation. With self-regulating power outputs and the ability to simultaneously charge up to four devices, it features an interchangeable tip system, with plentiful options.
A pack of six standard tips are supplied: iPhone/iPod, miniUSB, microUSB and recent Sony Ericsson, Samsung and Nokia adapters. A further 16 tips are available and customers can opt upon purchase for their custom choice of four rather than the standard six. Bought separately, the tips cost £6 each, so it’s worth getting the ones you need in the first place. And they’re not all for phones either, there’s one tip that houses a couple of AA/AAA rechargeable batteries.
The hub unit accommodates three tips – two at the back and one at the front. With each port having a button either side to release each tip, detachment from the hub from accidental knocks is extremely unlikely. In place, the tips protrude from the hub with LED status lights next to each that glow red when a device is on charge and, you guessed it, green when not.
Unfortunately, when power is on, these lights are always green, so if your device is nudged and breaks the connection, it’ll probably look like it’s fully replenished.

The side USB port can charge other devices, with the right cable, of course
Also, for those with more obscure mobile devices, a USB port on the side allows you to hook up other gear. This port lacks the audio-visual charge notifications of the main adapters, so you’ll have to rely on your device to tell you how charged it is. In tests, the standard pack of tips only covered half of my devices, so the USB port was used frequently, but due to cable use, appears no different to using a port on your laptop. That said, given the iDapt i4’s 13W total output, it knocks out a bit more juice than a typical PC port.