This article is more than 1 year old
Olympus LS-5 linear PCM recorder
Sound idea?
Sound Check
Audio mode is rather more interesting because it turns the LS-5 into a USB microphone. However, tests in this mode proved rather unreliable. When recording in both Sonority and Garageband, rather granular distortion crept in and wandered off again like dodgy FM reception. The buffering latency also went a bit haywire, going from its default delay at the bounds of acceptability to about half a second, with some noise added for good measure, and then back to normal again. Work in progress, evidently.
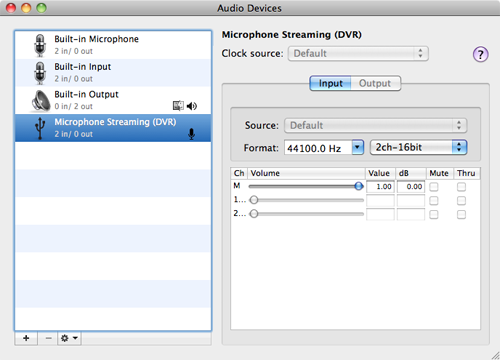
In Audio mode, the recorder can function as a USB stereo microphone
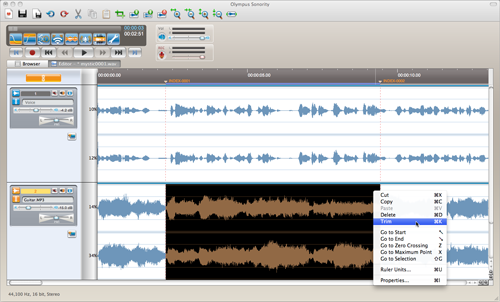
Talking of which, use Sonority for any length of time and you’ll come to the conclusion that people who design dictation machines really have no idea about what makes a good audio editor. While this application does, surprisingly, allow layering of multiple tracks, it doesn’t have a loop/cycle function. It has a sprinkling of effects yet has the audacity to charge for more useful effects that the open source application, er, Audacity offers for free.
Sonority: a bit of a clanger really – the effects offered for free are barely adequate
Click for a larger image
Also, if you fancy recording directly using the LS-5 as a USB mic, the only way you know what the input levels are, is when you start recording. Prior to that, there’s no input monitoring or pause/standby function. The real killer is playback. Hit the spacebar and away it goes, hit again – it’s going to stop, right? Nope, it keeps playing. It’s Shift-Spacebar to stop. WTF? Somebody at Olympus needs shooting, and given that this division works with dictators, you never know your luck.
As a standalone recorder, the performance is pretty much identical to the LS-10. Choose the right mode and recording is clean and well-defined and easily configured, thanks to the handy controls on the side for recording level, along with switches for mic sensitivity and low cut filter.