This article is more than 1 year old
Google patents search that tracks your mouse moves
Hover-over-but-don't-click-through rate
Google has patented a system that displays search results and ads based on where you move your mouse.
Mountain View first filed for the patent — dubbed a "system and method for modulating search relevancy using pointer activity monitoring" — in February 2005, and the US patent office rubber-stamped the application earlier this month, as noticed by TechEye.
Search engines such as Google's already order search results according to click-through rates — i.e., how often users click on particular hyperlinks. The new patent takes this idea a (large) step further, looking to reorder search results by monitoring when users show interest in web content without actually clicking on it.
"If the information being sought...is already available...in the search results (i.e., not requiring the user to click though to receive additional information), [today's] search engine may not receive user feedback about the relevancy of the informational item to the search," reads the patent-speak.
"There is a need for collecting user feedback with respect to informational items presented in response to a search query and adjusting the relevancy values of the items in accordance with the user feedback, even if there is no click through information about one or more of the informational items."
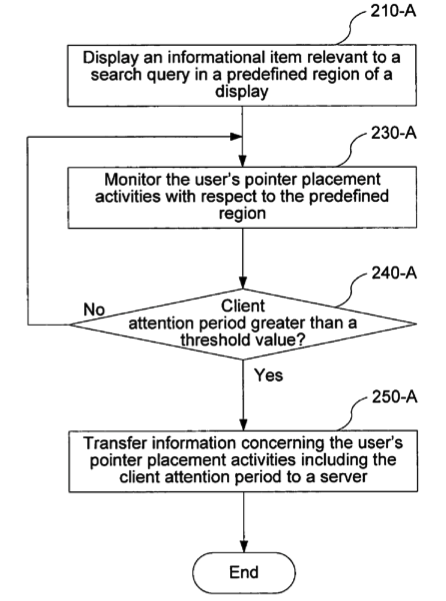
According to the patent, this involves somehow putting a piece of client software on the user's machine. "A client assistant residing in a client computer monitors movements of a user controlled pointer in a web browser, e.g., when the pointer moves into a predefined region and when it moves out of the predefined region," the patent says.
"A server then determines a relevancy value between an informational item associated with the predefined region and a search query according to the pointer hover period."
Presumably, if Google actually put this system into play, it would require the user to opt-in to such a client. But it seems that this tracking could also be done without client software, via JavaScript.
Google's application was the continuation of an earlier application filed in December 2004. According to the patent, users often hover over links before deciding to click on them. "Sometimes, a user may review multiple informational items responsive to a search query, moving a pointer over or near each of the informational items that the user reviews," it reads.
"These various pointer activities can provide another way to evaluate the user's feedback with respect to a particular informational item. A longer pointer hover period may suggest a more positive opinion from the user about the relevance between the informational item and the user's interest. Sometimes, a particular pointer movement pattern may provide additional information about a user's interest."
This includes, well, moving the pointer across a piece of text line by line at a normal reading speed.
Should Google start taking such behavior, we can assume that somewhere, someone will attempt to game the system. You might call it hover fraud. ®
