This article is more than 1 year old
Creative ZiiSound D5 wireless speakers
iOS-friendly Bluetooth music box
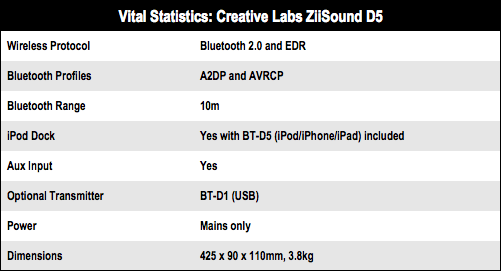
The BT-D5 is specifically designed to plug into the dock connector on an iPod, iPad or iPhone, so it won’t work with mobile phones or portable devices from companies other than Apple. There is a USB version of the transmitter, called the BT-D1. This will allow you to use the apt-X codec with any computer that has a USB port, but it costs an extra £40, which pushes the total price well over the £300 mark.

BT-D5 Apple-friendly dongle, a USB alternative is an optional extra
Pairing the D5 with a Bluetooth device is very simple, as you simply touch the ‘Connect’ control on the front of the speaker for about three seconds to make it enter pairing mode and then activate the Bluetooth feature on your phone or other device.
The audio quality using standard Bluetooth is very good. The main weakness is the lack of a sub-woofer – the bass output at lower levels is quite weak, although there’s a port on the back of the speaker unit that does help to add a bit of resonance to the sound once you push the volume up a bit.
The touch-sensitive volume control is rather slick, displaying a trail of lights as you slide your finger over the control panel. The sound quality does start to become distorted once you push the volume control past about 80 per cent – but that was also the point at which I started to worry about annoying the neighbours, so I probably wouldn’t go much higher than that anyway.
That said, the D5 isn’t powerful enough for a full-on party, but it’ll do very nicely if you want to invite some friends around for dinner or a BBQ in the garden. The Bluetooth reception is also very good. Creative claims that the Bluetooth range is up to 10m ‘in open space’, but I was able to wander from room to room at home with my iPod Touch without the slightest interruption to the streaming audio.