This article is more than 1 year old
Apple Mac Mini 2010
Makes other SFF PCs look like towers
If you flip the Mini over, you’ll see that the base plate can be removed, so that you no longer need to perform open-heart surgery with a putty-knife in order to perform a memory upgrade.

The insides are more accessible than before
Peering around the back you’ll see a Mini DisplayPort interface alongside the HDMI, and Apple also includes an HDMI-to-DVI adaptor in the box so that you can use it with a DVI monitor. Don’t forget that the Mac Mini is sold without monitor, keyboard or mouse. Apple clearly feels the new Mini is going to sit on desktops as well as the space next to someone's TV.
Another newcomer is the SD card slot – inconveniently positioned on the rear – alongside a set of four USB ports, Gigabit Ethernet, Firewire 800 and digital audio in/out.
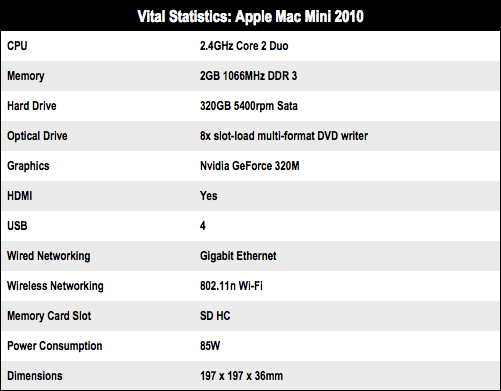
But while Apple has really gone to town with the engineering and aesthetic aspects of the Mini, a closer look at the spec sheet shows that it has cut a few recessionary corners in other areas. The Mac Mini released towards the end of 2009 was available in two configurations: the entry-level model cost £529 with 2.26GHz Core 2 Duo processor and 2GB of Ram, or you could increase the processor speed to 2.53GHz and double up to 4GB Ram for £649.
In contrast, this new model is available in just one main configuration that costs £649 with a 2.4GHz Core 2 Duo - no Core i3 or i5 here - and 2GB of memory, albeit 1066MHz DDR 3.