This article is more than 1 year old
iPad's brain not so unique
A4 core coming to Android?
Taking the tear-down to the microscopic level, UBM TechInsights concludes that Apple's A4 processor is manufactured by Samsung and will share a core with that company's next Android handset.
The A4 is used in the iPad as well as the next-generation iPhone announced on Monday, and is generally considered to be the product of Apple's purchase of PA Semi in 2008.
Most of Apple's application processors are manufactured by Samsung, as UBM TechInsights has already established (pdf), but this time they've been busy comparing the A4 processor to the one used in the Samsung Wave, and reckon there's a fair bit of overlap.
In common with almost all smartphones both the Wave and the iPhone have two processors: one running a real-time OS and handling radio communications, while the other runs something a little more consumer-friendly and is used to host applications running on the phone. Alone among smartphone operating systems, Symbian can support proper real time radio functions, making a single-processor smartphone possible... but still not very desirable.
Both the A4 and the S5PC110A01 are ARM based - again in common with just about every smart phone out there - and a very-close-up view of the chips shows what appears to be exactly the same ARM core in both:
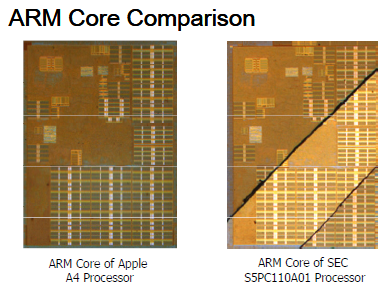
A comparison slide from UBM TechInsight's detailed analysis (pdf)
Being as the S5PC110A01 is using an ARM Cortex A8 core, UBM Concludes that Apple is using the same thing, and the same scale of production (45 nanometre). Given the chip is already being used in the Samsung Wave it makes sense that it will turn up in the company's next Android offering, the Galaxy S.
The processor is, of course, a lot more than its core. The Wave uses Imagination Technology's PowerVR SGX 3D video engine on the same die. Apple uses the same family, though exactly which model remains hard to prove.
But this does mean that Samsung is getting really good economies of scale manufacturing that core at least, and that we'll soon be able to see Android and iOS running side by side on the same processor, which should prove interesting. ®
