This article is more than 1 year old
Apple patent shows iPhone ruling the home
In your living room? NFC
Apple has patented using an NFC-equipped iPhone to set up links between electronic devices, hinting at how the company sees the future of the living room and its part there.
The recently published patent covers the use of an iPhone to connect to various consumer devices, including speakers, televisions and set-top boxes. The plan calls for an initial connection (over Near Field Communication - low-power, short-range, radio - or similar) for the exchange of credentials. This is then used to download a client application from the internet, and to discover an internet address over which a client/service connection can be established.
Even if the patent fails against prior art, which seems probable at an ill-educated glance, it serves to demonstrate how Apple sees televisions and stereo systems becoming mere peripherals manufactured by companies entirely beholden to Apple's largesse.
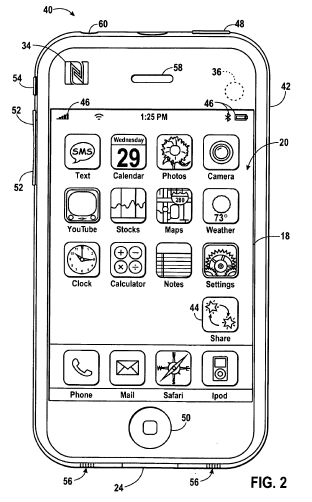
Note the NFC Forum logo in the top left (numbered 34)
The idea that a television is just a screen available to anything that wishes to display - while a stereo system fulfils the same role for audio streams - is nothing new. Much of the Bluetooth protocol is concerned with how devices advertise their capabilities and how clients request use of offered services. Apple's extension to that is for the serving device to provide only URLs to the client (over NFC, or even using a QR Code) from which more information and a client application or driver can be downloaded.
The examples in the patent include tapping an iPhone against a keyboard to exchange a URL over NFC. That URL then provides the name of the keyboard and suggests using a Bluetooth connection. Another example shows the iPhone being tapped against a TV, whereupon the URL provides an IP address and a client application to download. The eventual connection is an IP link for streaming video.
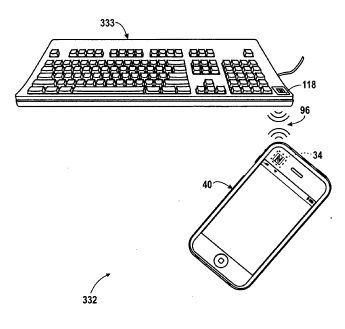
You'll still need a keyboard driver, and an application to use it, but at least pairing will be easy
NFC isn't essential to the process - bar codes and other short-range communications are referenced - but the presence of the NFC Forum logo on the device indicates Cupertino's interest in the standard. Equally, the misspelling of "TransferJet" (which is made plural) could indicate a lack of interest in Sony's proprietary wideband technology.
A reference to NFC communication taking place over "magnetic field induction" shows the author's lack of technical experience - induction may be used to power NFC, but isn't used for communication these days. But perhaps we're reading too much into these details.
We do know that Apple has been taking an interest in NFC of late, and that other manufacturers have proved reluctant to embed technology that lacks a killer application. This patent outlines a world where your iPhone can be tapped against your TV to automatically download a remote control application, but one where the manufacturer only needs to apply a sticker to make that happen.
Not only could Apple drive NFC adoption (who would want to use a sticker when the competition is using taps?) but with every remote control and streaming client going through Apple's iTunes approval process it would give Cupertino an unprecedented level of control over what goes on in your living room.
We've suggested before that putting NFC into an iPhone would expose Apple to a level of risk with which Cupertino wouldn't be comfortable, despite the fact that it's a really good idea. But if Apple isn't planning something along those lines then it's certainly going a long way to ensure no one else does.
It's unlikely a patent like this will go unchallenged, and we wouldn't want to bet on the result of such a challenge, but if Apple really does deploy this kind of capability with its next iPhone then we might even have to buy one - just for evaluation purposes, obviously. ®
